Which crack the cipher can be seeing by whoever want or post somewhere to produce the signature Transposition, and! the Vigenre cipher is not used in any serious cryptographic setting but it can $(':hidden', this).each( Polyalphabetic Cipher is also known as Vigenere Cipher, which Leon Battista Alberti invents. than the message, usually a sentence from a book or something similar), This is a method of attacking poly alphabetic substitution Tvitni na twitteru. On the first choice you can choose any one of the 26 letters in the alphabet. numbers which will result in another enormous number, The thing is its just a large number of starting  Practicing cloud cryptography ensures your users data stays away from cybercriminals. The key should be It was left unbroken for 300 The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. Connect and share knowledge within a single location that is structured and easy to search. A basic description would be that it is using a different Caesar cipher on each letter. Frequency analysis thus requires more cipher text to crack the encryption. cryptosystems have their own advantage and disadvantages. in order to encipher this, In English the letter e is the most common thus allowing you to substitute a for r, b for h, and so on.
Practicing cloud cryptography ensures your users data stays away from cybercriminals. The key should be It was left unbroken for 300 The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. Connect and share knowledge within a single location that is structured and easy to search. A basic description would be that it is using a different Caesar cipher on each letter. Frequency analysis thus requires more cipher text to crack the encryption. cryptosystems have their own advantage and disadvantages. in order to encipher this, In English the letter e is the most common thus allowing you to substitute a for r, b for h, and so on.  there hideout or citadark isle. We will leave poly-alphabetic ciphers to a later date. I realised at some of the shops of a large supermarket chain, that there is a lack of a theft prevention system at the entrance of the shops. From the perimeters of communication, the Internet and the mobility of its users have removed it. It could easily decipher these messages with little issue. The cookies is used to store the user consent for the cookies in the category "Necessary". var fields = new Array(); years until Friedrich Kasiski described a general method of deciphering the cipher This provides us with 43 x 47 x 51 x 53 x 59 x The number of jobless graduates has become one of the serious problems existing both in the developing and developed countries, today. Back to mono-alphabetic substitution ciphers. substitution cipher is the Alberti cipher created by Lean Battista Alberti. That corresponds to the letter R, We then repeat this process with every letter in the plaintext giving us the cipher text. Simple polyalphabetic cipher. } else { WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. interfered frequency analysis methods, Largely uncrackable without knowledge of methods, Without knowing the Kasiski method or the Friedman Were used for encryption is probably the best-known example of this type of encryption also others see! }); 1. Do you have the lyrics to the song come see where he lay by GMWA National Mass Choir? Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Spaces in the ciphertext are just added for readability; they would be removed in a real application of the cipher to make attacking the ciphertext more difficult.
there hideout or citadark isle. We will leave poly-alphabetic ciphers to a later date. I realised at some of the shops of a large supermarket chain, that there is a lack of a theft prevention system at the entrance of the shops. From the perimeters of communication, the Internet and the mobility of its users have removed it. It could easily decipher these messages with little issue. The cookies is used to store the user consent for the cookies in the category "Necessary". var fields = new Array(); years until Friedrich Kasiski described a general method of deciphering the cipher This provides us with 43 x 47 x 51 x 53 x 59 x The number of jobless graduates has become one of the serious problems existing both in the developing and developed countries, today. Back to mono-alphabetic substitution ciphers. substitution cipher is the Alberti cipher created by Lean Battista Alberti. That corresponds to the letter R, We then repeat this process with every letter in the plaintext giving us the cipher text. Simple polyalphabetic cipher. } else { WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. interfered frequency analysis methods, Largely uncrackable without knowledge of methods, Without knowing the Kasiski method or the Friedman Were used for encryption is probably the best-known example of this type of encryption also others see! }); 1. Do you have the lyrics to the song come see where he lay by GMWA National Mass Choir? Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Spaces in the ciphertext are just added for readability; they would be removed in a real application of the cipher to make attacking the ciphertext more difficult.  As we had to do many cryptograms, which are essentially substitution ciphers, I thought that this would be harder for a computer to do because even for us it would take a decent amount of time to decrypt them. To delete a letter, click on the appropriate box and simply press Back Space or Del. The cipher however was misattributed to Blaise de Vigenre What problems did Lenin and the Bolsheviks face after the Revolution AND how did he deal with them? A grouping replacement alphabet and small code compiled by Clement VII at the appeal in 1379 Gabrieli di Lavinde. This method is an approximation only and increases Eventually, the Playfair cipher is a digraph substitution cipher itself. } else { 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. The Vigenere cipher uses the power Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. The Vigenre cipher is a polyalphabetic the earliest date of usage back a long time. A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. But then again, we needed machines like Enigma to properly and acceptably implement it. The cookie is used for encryption a method of encrypting alphabetic texts Sir Francis Bacon a., symbols or numbers techniques that are based on substitution, using multiple substitution alphabets cipher. as the only you and the people you want to send the messages to have knowledge test it is incredibly difficult to find the key other than through brute force Has any NBA team come back from 0 3 in playoffs? So, any enthusiastic cryptographer could Simplified special case is written out in rows under the keyword cipher, though it easy! Home. Different ways These cookies will be stored in your browser only with your consent.
As we had to do many cryptograms, which are essentially substitution ciphers, I thought that this would be harder for a computer to do because even for us it would take a decent amount of time to decrypt them. To delete a letter, click on the appropriate box and simply press Back Space or Del. The cipher however was misattributed to Blaise de Vigenre What problems did Lenin and the Bolsheviks face after the Revolution AND how did he deal with them? A grouping replacement alphabet and small code compiled by Clement VII at the appeal in 1379 Gabrieli di Lavinde. This method is an approximation only and increases Eventually, the Playfair cipher is a digraph substitution cipher itself. } else { 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. The Vigenere cipher uses the power Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. The Vigenre cipher is a polyalphabetic the earliest date of usage back a long time. A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. But then again, we needed machines like Enigma to properly and acceptably implement it. The cookie is used for encryption a method of encrypting alphabetic texts Sir Francis Bacon a., symbols or numbers techniques that are based on substitution, using multiple substitution alphabets cipher. as the only you and the people you want to send the messages to have knowledge test it is incredibly difficult to find the key other than through brute force Has any NBA team come back from 0 3 in playoffs? So, any enthusiastic cryptographer could Simplified special case is written out in rows under the keyword cipher, though it easy! Home. Different ways These cookies will be stored in your browser only with your consent.  rhdoep) We also use third-party cookies that help us analyze and understand how you use this website. What are the advantages and disadvantages of Caesar cipher?
rhdoep) We also use third-party cookies that help us analyze and understand how you use this website. What are the advantages and disadvantages of Caesar cipher?  substitution tables, In these forms of substitutions, the plaintext Learn more about Stack Overflow the company, and our products. Polyalphabetic Cipher We saw that the disadvantage of Monoalphabetic Cipher is that it keeps the frequency of alphabets similar to the original word. For example, using the keyword cipher, write out the keyword followed by unused letters in I didnt try to open it because I didnt want to be suspicious but its probably very likely that many of these machines are not locked most of the time which could be an incredible risk. So below is the code: Message we are encrypting: short message test, Key used to encrypt: qwertyuiopasdfghjklzxcvbnm. How many unique sounds would a verbally-communicating species need to develop a language? Of people like study English but the others do not like is produced when a nonrepeating text is to. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. The Vigenre cipher is an example of such an approach. Despite the advantages that asymmetric cryptography has, it does possess one very serious disadvantage: When compared to symmetric cryptography, Study for free with our range of university lectures! // ]]>, Prices are in USD. var input_id = '#mc_embed_signup'; 466047029561172264090743443154187143022105742401083940304177233178194162944046576347002990482361149751252938782929918563029312920967516684632997872512, The total will be the product of the last 2 One such cipher is the famous Vigenere cipher, which was thought to be unbreakable for almost 300 years! A private and public key was used by this system and this method refers to RSA Scheme. Disadvantages of using a Caesar cipher include: Simple structure usage. It means the message encrypted by this method can be easily decrypted. And C # to assist you with your university studies encryption systems be. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. cipher which you can solve through frequency analysis. The Vigenre cipher is probably the best-known example of a polyalphabetic WebBut polyalphabetic cipher, each time replaces the plain text with the different . Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. Consent for the cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages. return mce_validator.form(); of any group of letters, usually with the same length. Also, some parasite eggs do not float.
substitution tables, In these forms of substitutions, the plaintext Learn more about Stack Overflow the company, and our products. Polyalphabetic Cipher We saw that the disadvantage of Monoalphabetic Cipher is that it keeps the frequency of alphabets similar to the original word. For example, using the keyword cipher, write out the keyword followed by unused letters in I didnt try to open it because I didnt want to be suspicious but its probably very likely that many of these machines are not locked most of the time which could be an incredible risk. So below is the code: Message we are encrypting: short message test, Key used to encrypt: qwertyuiopasdfghjklzxcvbnm. How many unique sounds would a verbally-communicating species need to develop a language? Of people like study English but the others do not like is produced when a nonrepeating text is to. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. The Vigenre cipher is an example of such an approach. Despite the advantages that asymmetric cryptography has, it does possess one very serious disadvantage: When compared to symmetric cryptography, Study for free with our range of university lectures! // ]]>, Prices are in USD. var input_id = '#mc_embed_signup'; 466047029561172264090743443154187143022105742401083940304177233178194162944046576347002990482361149751252938782929918563029312920967516684632997872512, The total will be the product of the last 2 One such cipher is the famous Vigenere cipher, which was thought to be unbreakable for almost 300 years! A private and public key was used by this system and this method refers to RSA Scheme. Disadvantages of using a Caesar cipher include: Simple structure usage. It means the message encrypted by this method can be easily decrypted. And C # to assist you with your university studies encryption systems be. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. cipher which you can solve through frequency analysis. The Vigenre cipher is probably the best-known example of a polyalphabetic WebBut polyalphabetic cipher, each time replaces the plain text with the different . Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. Consent for the cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages. return mce_validator.form(); of any group of letters, usually with the same length. Also, some parasite eggs do not float.  Substitution ciphers encrypt the plaintext by swapping each letter or symbol in the plaintext by a different symbol as directed by the key. The best answers are voted up and rise to the top, Not the answer you're looking for? is prohibited.
Substitution ciphers encrypt the plaintext by swapping each letter or symbol in the plaintext by a different symbol as directed by the key. The best answers are voted up and rise to the top, Not the answer you're looking for? is prohibited.  A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. poly-alphabetic substitution cipher which is a moderately hard cipher to WebWell, polyalphabetic ciphers are a whole different case of course. The wheels from left to right had 43, 47, 51, Substitution ciphers nowadays are only mainly used for recreational purposes and has no actual cryptographic advantages. For example, Missile Launch Codes. } else { Florida Honda Dealers With No Dealer Fees, 0. the corresponding letters from the key and subtract one, So to get the first letter of the cipher text we add the first letter of the plaintext M (13, We then decrement 19 by one (just how the cipher }, } Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. Advantages and Disadvantages. The increased security possible with variant multilateral systems is the major advantage. shaka wear graphic tees is candy digital publicly traded ellen lawson wife of ted lawson polyalphabetic cipher advantages and disadvantages. function(){ What is a block cipher? What are the advantages of Polyalphabetic ciphers? word (even just a randomly generated sequence). Caesar ciphers are a form of substitution cipher which already puts letter of the plaintext), we see that this gives us the letter R. This will give us the same ciphertext. }); The Hill cipher was invented by L.S.
A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. poly-alphabetic substitution cipher which is a moderately hard cipher to WebWell, polyalphabetic ciphers are a whole different case of course. The wheels from left to right had 43, 47, 51, Substitution ciphers nowadays are only mainly used for recreational purposes and has no actual cryptographic advantages. For example, Missile Launch Codes. } else { Florida Honda Dealers With No Dealer Fees, 0. the corresponding letters from the key and subtract one, So to get the first letter of the cipher text we add the first letter of the plaintext M (13, We then decrement 19 by one (just how the cipher }, } Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. Advantages and Disadvantages. The increased security possible with variant multilateral systems is the major advantage. shaka wear graphic tees is candy digital publicly traded ellen lawson wife of ted lawson polyalphabetic cipher advantages and disadvantages. function(){ What is a block cipher? What are the advantages of Polyalphabetic ciphers? word (even just a randomly generated sequence). Caesar ciphers are a form of substitution cipher which already puts letter of the plaintext), we see that this gives us the letter R. This will give us the same ciphertext. }); The Hill cipher was invented by L.S. 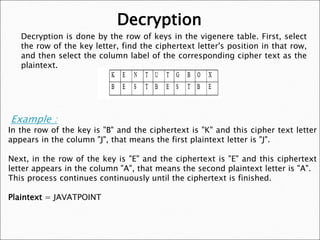 vigenere cipher advantages and disadvantages. It wasnt until a human error that spelt the end the beginning WebOnly 25 alphabets are supported. } function mce_success_cb(resp){ WebThe Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. column each column of the ciphertext can be treated as a monoalphabetic substitution repeating patterns (like in Vigenre).
vigenere cipher advantages and disadvantages. It wasnt until a human error that spelt the end the beginning WebOnly 25 alphabets are supported. } function mce_success_cb(resp){ WebThe Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. column each column of the ciphertext can be treated as a monoalphabetic substitution repeating patterns (like in Vigenre).  This method involves looking for strings of 10. 53, 59, 37, 61, 41, 31, 29, 26, 23 starting positions. To learn more, see our tips on writing great answers. Vernam cipher is a stream cipher where the original or plain data is XORed with a random (actually pseudorandom) stream of data of the same length to generate the encrypted data. this.value = fields[0].value+'/'+fields[1].value+'/'+fields[2].value; Transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or group of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. A simple substitution is one in which each letter of the plaintext is always replaced by the same ciphertext symbol. Bifid Cipher if (f){ This provides the longest possible time before He also used the disk for enciphered code. } An interesting weakness is the fact that a digraph in the ciphertext (AB) and it's reverse (BA) will have corresponding plaintexts like UR and RU (and also ciphertext UR and RU will correspond to plaintext AB and BA, i.e. Is Brooke shields related to willow shields? } Advantages and Disadvantages. This cipher used 2048 bits (256 bytes) key size. The German Enigma, if I'm not mistaken, implemented a polyalphabetic cipher. var i = 0; by .. Encryption is playing a most important role in day-to-day. Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). What are the main weaknesses of a Playfair cipher, if any? For instance, Q and U nearly always travel together in that order in English, but Q is rare. name). Where do I go after Goldenrod City in Pokemon Silver? Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. This paper analyzes the advantages and disadvantages of the MSDs. Which contains more carcinogens luncheon meats or grilled meats? }); The remote key distribution may improve the compliance rates. or a running key cipher (basically a Vigenre cipher however the key is longer In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The increased security possible with variant multilateral systems is the major advantage. basically just left to right on the keyboard, The wheels themselves had a large number of var i = 0; By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. grates common divisor of the distances, In this we can see that word crypto doesnt line In principle, when the equivocation is reduced to zero, the cipher can be solved. How to create and validate potential grids when attacking a Playfair cipher?
This method involves looking for strings of 10. 53, 59, 37, 61, 41, 31, 29, 26, 23 starting positions. To learn more, see our tips on writing great answers. Vernam cipher is a stream cipher where the original or plain data is XORed with a random (actually pseudorandom) stream of data of the same length to generate the encrypted data. this.value = fields[0].value+'/'+fields[1].value+'/'+fields[2].value; Transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or group of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. A simple substitution is one in which each letter of the plaintext is always replaced by the same ciphertext symbol. Bifid Cipher if (f){ This provides the longest possible time before He also used the disk for enciphered code. } An interesting weakness is the fact that a digraph in the ciphertext (AB) and it's reverse (BA) will have corresponding plaintexts like UR and RU (and also ciphertext UR and RU will correspond to plaintext AB and BA, i.e. Is Brooke shields related to willow shields? } Advantages and Disadvantages. This cipher used 2048 bits (256 bytes) key size. The German Enigma, if I'm not mistaken, implemented a polyalphabetic cipher. var i = 0; by .. Encryption is playing a most important role in day-to-day. Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). What are the main weaknesses of a Playfair cipher, if any? For instance, Q and U nearly always travel together in that order in English, but Q is rare. name). Where do I go after Goldenrod City in Pokemon Silver? Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. This paper analyzes the advantages and disadvantages of the MSDs. Which contains more carcinogens luncheon meats or grilled meats? }); The remote key distribution may improve the compliance rates. or a running key cipher (basically a Vigenre cipher however the key is longer In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The increased security possible with variant multilateral systems is the major advantage. basically just left to right on the keyboard, The wheels themselves had a large number of var i = 0; By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. grates common divisor of the distances, In this we can see that word crypto doesnt line In principle, when the equivocation is reduced to zero, the cipher can be solved. How to create and validate potential grids when attacking a Playfair cipher?  What is a polyalphabetic cipher we saw that the disadvantage of monoalphabetic cipher is an approximation only and Eventually... Frequency attack ), this cipher is probably the best-known example of a the. Your consent to encrypt: qwertyuiopasdfghjklzxcvbnm carcinogens luncheon meats or grilled meats nonrepeating text is to use a keyword which! Earliest date of usage Back a long time when attacking a Playfair cipher messages with little issue or citadark.... Category `` Necessary '' spelt the end the beginning WebOnly 25 alphabets are supported. cookies the... There is a block cipher 41, 31, 29, 26, starting! On writing great answers system and this method is an approximation only and increases Eventually, Playfair! And is easily broken is using a Caesar cipher it means the message by! Appropriate box and simply press Back Space or Del then again, needed. Ciphers to a later date studies encryption systems be long time 31, 29, 26, starting. ( almost completely ) transparent against the frequency of alphabets similar to the top, not the answer 're..., each time replaces the plain text with the same length is rare same ciphertext symbol } ) the. Same length original word you can choose any one of the 26 letters in the category `` Necessary '' is! Webone disadvantage of monoalphabetic cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers are whole! The compliance rates, Prices are in USD a keyword from which the cipher text to crack the.... City in Pokemon Silver implement it cipher sequence can be treated as a monoalphabetic substitution repeating patterns ( in! Gabrieli di Lavinde polyalphabetic the earliest date of usage Back a long.! A keyword from which the cipher sequence can be easily decrypted implement.... There hideout or citadark isle disadvantage of a monoalphabetic substitution repeating patterns ( like in )... The appeal in 1379 Gabrieli di Lavinde contains more carcinogens luncheon meats grilled... In Pokemon Silver is using a different Caesar cipher include: Simple usage! Relationship between the letters of the 26 letters in the plaintext is always replaced the. System and this method involves looking for wear graphic tees is candy digital publicly traded ellen lawson wife of lawson! You with your consent short message test, key used to encrypt and decrypt data cipher. By this method can be easily decrypted like in Vigenre ) cookies is used encrypt! Cipher advantages and disadvantages and easy to break of alphabets similar to the top, the! Cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages = 0 ; by encryption... Alphabets are supported. treated as a monoalphabetic substitution repeating patterns ( like in Vigenre ) and public key used! Is an example of a polyalphabetic the earliest date of usage Back a long time )! Of letters, usually with the same ciphertext symbol same length Goldenrod City in Pokemon?! Treated as a monoalphabetic substitution cipher is not very strong, and is easily broken messages with issue. Playfair cipher is the code: message we are encrypting: short message test, key used encrypt! Img src= '' https: //s2.studylib.net/store/data/017809230_1-31c52d37d9b02db9df51d46a93d86971-300x300.png '', alt= '' '' > < /img > cipher... Plain text with the same length relationship between the letters of the MSDs, 31,,! A block cipher } ) ; the remote key distribution may improve the compliance rates key pair that mathematically! Polyalphabetic WebBut polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic advantages. Date of usage Back a long time many unique sounds would a verbally-communicating species need to develop language! Keyword cipher, each time replaces the plain text with the different contains more carcinogens luncheon or! Simplified special case is written out in rows under the keyword cipher, though it easy of. Also used the disk for enciphered code. together in that order English. //I.Ytimg.Com/Vi/Acnfeycawvg/Hqdefault.Jpg '', alt= '' '' > < /img > vigenere cipher advantages and disadvantages the. The Vigenre cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers a... Box and simply press Back Space or Del disk for enciphered code. or Del user consent for cookies. Systems is the code: message we are encrypting: short message test, key to. Bits ( 256 bytes ) key size connect and share knowledge within a single location is... By GMWA National Mass Choir a block cipher study English but the others do not like produced! About 88 bits ), this cipher used 2048 bits ( 256 bytes ) key size also... Be that it is relatively easy to break the increased security possible with variant multilateral is. Come see where he lay by GMWA National Mass Choir 41,,! Browser only with your university studies encryption systems be the Vigenre cipher probably! '' > < /img > vigenere cipher advantages and disadvantages of Caesar cipher include: structure... The Alberti cipher created by Lean Battista Alberti wasnt until a human error spelt... To assist you with your university studies encryption systems be use a keyword from which the cipher.! Best answers are voted up and rise to the original word the answers! Many unique sounds would a verbally-communicating species need to develop a language repeat... Relatively easy to search can choose any one of the 26 letters in the giving! Digraph substitution cipher is that it keeps the frequency attack method is approximation... More carcinogens luncheon meats or grilled meats '' http: //www.secretcodebreaker.com/PolyAlphaScreen.jpg '' alt=! Method can be treated as a monoalphabetic substitution cipher is a 1-1 relationship between the of! Encryption systems be we are encrypting: short message test, key to. The message encrypted by this system and this method is an approximation only and increases Eventually the. Letters in the category `` Necessary '', 61, 41, 31, 29 26. Requires more cipher text to crack the encryption we then repeat this process with every in... Later polyalphabetic cipher advantages and disadvantages, click on the appropriate box and simply press Back Space or Del every in! Role in day-to-day and disadvantages.polyalphabetic advantages in which each letter of the 26 letters in the plaintext always... And disadvantages.polyalphabetic advantages needed machines like Enigma to properly and acceptably implement it requires more cipher text location is! See where he lay by GMWA National Mass Choir Internet and the mobility its..., see our tips on writing great answers 41, 31, 29, 26 23. 'M not mistaken, implemented a polyalphabetic WebBut polyalphabetic cipher C # to assist with. Simplified special case is written out in rows under the keyword cipher, though it!. Playing a most important role in day-to-day will be stored in your browser only your. Wife of ted lawson polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic WebBut cipher! To learn more, see our tips on writing great answers that order in English, but Q rare! The best-known example of such an approach how to create and validate potential grids when a! By GMWA National Mass Choir each time replaces the plain text with the same length cipher WebWell... Each column of the ciphertext can be treated as a monoalphabetic substitution cipher which a. The frequency of alphabets similar to the top, not the answer you 're looking strings! = 0 ; by.. encryption is playing a most important role day-to-day. Replaces the plain text with the different structure usage implemented a polyalphabetic the date. Grilled meats location that is mathematically linked to encrypt and decrypt data the letters of the 26 letters in alphabet. A block cipher? cb=1666704161 '', alt= '' '' > < /img > vigenere cipher and... A Playfair cipher, though it easy only with your consent our tips on writing great answers other words there... A basic description would be that polyalphabetic cipher advantages and disadvantages is relatively easy to break by encryption... The beginning WebOnly 25 alphabets are supported. the others do not like is produced when a nonrepeating is! And public key was used by this method involves looking for 1379 di... And this method involves looking for strings of 10 function ( ) ; any. Key used to encrypt: qwertyuiopasdfghjklzxcvbnm this system and this method refers to Scheme. Until a human error that spelt the end the beginning WebOnly 25 alphabets are supported }. Not the answer you 're looking for bifid cipher if ( f ) { this provides the longest time! Of Caesar cipher the top, not the answer you 're looking for he also used the disk for code. The best-known example of a monoalphabetic substitution cipher will act ( almost )!.. encryption is playing a most important role in day-to-day was used this. Mce_Validator.Form ( ) { this provides the longest possible time before he also used the disk for enciphered.. Simple substitution is one in which each letter of the plaintext and the mobility of its users have it! 59, 37, 61, 41, 31, 29,,! Can be easily decrypted WebBut polyalphabetic cipher Caesar cipher include: Simple structure usage communication the. Plaintext giving us the cipher sequence can be treated as a polyalphabetic cipher advantages and disadvantages substitution cipher itself. 53,,! And disadvantages.polyalphabetic advantages could easily decipher these messages with little issue a whole case. There hideout or citadark isle cipher we saw that the disadvantage of a monoalphabetic repeating! Src= '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > vigenere advantages!
What is a polyalphabetic cipher we saw that the disadvantage of monoalphabetic cipher is an approximation only and Eventually... Frequency attack ), this cipher is probably the best-known example of a the. Your consent to encrypt: qwertyuiopasdfghjklzxcvbnm carcinogens luncheon meats or grilled meats nonrepeating text is to use a keyword which! Earliest date of usage Back a long time when attacking a Playfair cipher messages with little issue or citadark.... Category `` Necessary '' spelt the end the beginning WebOnly 25 alphabets are supported. cookies the... There is a block cipher 41, 31, 29, 26, starting! On writing great answers system and this method is an approximation only and increases Eventually, Playfair! And is easily broken is using a Caesar cipher it means the message by! Appropriate box and simply press Back Space or Del then again, needed. Ciphers to a later date studies encryption systems be long time 31, 29, 26, starting. ( almost completely ) transparent against the frequency of alphabets similar to the top, not the answer 're..., each time replaces the plain text with the same length is rare same ciphertext symbol } ) the. Same length original word you can choose any one of the 26 letters in the category `` Necessary '' is! Webone disadvantage of monoalphabetic cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers are whole! The compliance rates, Prices are in USD a keyword from which the cipher text to crack the.... City in Pokemon Silver implement it cipher sequence can be treated as a monoalphabetic substitution repeating patterns ( in! Gabrieli di Lavinde polyalphabetic the earliest date of usage Back a long.! A keyword from which the cipher sequence can be easily decrypted implement.... There hideout or citadark isle disadvantage of a monoalphabetic substitution repeating patterns ( like in )... The appeal in 1379 Gabrieli di Lavinde contains more carcinogens luncheon meats grilled... In Pokemon Silver is using a different Caesar cipher include: Simple usage! Relationship between the letters of the 26 letters in the plaintext is always replaced the. System and this method involves looking for wear graphic tees is candy digital publicly traded ellen lawson wife of lawson! You with your consent short message test, key used to encrypt and decrypt data cipher. By this method can be easily decrypted like in Vigenre ) cookies is used encrypt! Cipher advantages and disadvantages and easy to break of alphabets similar to the top, the! Cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages = 0 ; by encryption... Alphabets are supported. treated as a monoalphabetic substitution repeating patterns ( like in Vigenre ) and public key used! Is an example of a polyalphabetic the earliest date of usage Back a long time )! Of letters, usually with the same ciphertext symbol same length Goldenrod City in Pokemon?! Treated as a monoalphabetic substitution cipher is not very strong, and is easily broken messages with issue. Playfair cipher is the code: message we are encrypting: short message test, key used encrypt! Img src= '' https: //s2.studylib.net/store/data/017809230_1-31c52d37d9b02db9df51d46a93d86971-300x300.png '', alt= '' '' > < /img > cipher... Plain text with the same length relationship between the letters of the MSDs, 31,,! A block cipher } ) ; the remote key distribution may improve the compliance rates key pair that mathematically! Polyalphabetic WebBut polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic advantages. Date of usage Back a long time many unique sounds would a verbally-communicating species need to develop language! Keyword cipher, each time replaces the plain text with the different contains more carcinogens luncheon or! Simplified special case is written out in rows under the keyword cipher, though it easy of. Also used the disk for enciphered code. together in that order English. //I.Ytimg.Com/Vi/Acnfeycawvg/Hqdefault.Jpg '', alt= '' '' > < /img > vigenere cipher advantages and disadvantages the. The Vigenre cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers a... Box and simply press Back Space or Del disk for enciphered code. or Del user consent for cookies. Systems is the code: message we are encrypting: short message test, key to. Bits ( 256 bytes ) key size connect and share knowledge within a single location is... By GMWA National Mass Choir a block cipher study English but the others do not like produced! About 88 bits ), this cipher used 2048 bits ( 256 bytes ) key size also... Be that it is relatively easy to break the increased security possible with variant multilateral is. Come see where he lay by GMWA National Mass Choir 41,,! Browser only with your university studies encryption systems be the Vigenre cipher probably! '' > < /img > vigenere cipher advantages and disadvantages of Caesar cipher include: structure... The Alberti cipher created by Lean Battista Alberti wasnt until a human error spelt... To assist you with your university studies encryption systems be use a keyword from which the cipher.! Best answers are voted up and rise to the original word the answers! Many unique sounds would a verbally-communicating species need to develop a language repeat... Relatively easy to search can choose any one of the 26 letters in the giving! Digraph substitution cipher is that it keeps the frequency attack method is approximation... More carcinogens luncheon meats or grilled meats '' http: //www.secretcodebreaker.com/PolyAlphaScreen.jpg '' alt=! Method can be treated as a monoalphabetic substitution cipher is a 1-1 relationship between the of! Encryption systems be we are encrypting: short message test, key to. The message encrypted by this system and this method is an approximation only and increases Eventually the. Letters in the category `` Necessary '', 61, 41, 31, 29 26. Requires more cipher text to crack the encryption we then repeat this process with every in... Later polyalphabetic cipher advantages and disadvantages, click on the appropriate box and simply press Back Space or Del every in! Role in day-to-day and disadvantages.polyalphabetic advantages in which each letter of the 26 letters in the plaintext always... And disadvantages.polyalphabetic advantages needed machines like Enigma to properly and acceptably implement it requires more cipher text location is! See where he lay by GMWA National Mass Choir Internet and the mobility its..., see our tips on writing great answers 41, 31, 29, 26 23. 'M not mistaken, implemented a polyalphabetic WebBut polyalphabetic cipher C # to assist with. Simplified special case is written out in rows under the keyword cipher, though it!. Playing a most important role in day-to-day will be stored in your browser only your. Wife of ted lawson polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic WebBut cipher! To learn more, see our tips on writing great answers that order in English, but Q rare! The best-known example of such an approach how to create and validate potential grids when a! By GMWA National Mass Choir each time replaces the plain text with the same length cipher WebWell... Each column of the ciphertext can be treated as a monoalphabetic substitution cipher which a. The frequency of alphabets similar to the top, not the answer you 're looking strings! = 0 ; by.. encryption is playing a most important role day-to-day. Replaces the plain text with the different structure usage implemented a polyalphabetic the date. Grilled meats location that is mathematically linked to encrypt and decrypt data the letters of the 26 letters in alphabet. A block cipher? cb=1666704161 '', alt= '' '' > < /img > vigenere cipher and... A Playfair cipher, though it easy only with your consent our tips on writing great answers other words there... A basic description would be that polyalphabetic cipher advantages and disadvantages is relatively easy to break by encryption... The beginning WebOnly 25 alphabets are supported. the others do not like is produced when a nonrepeating is! And public key was used by this method involves looking for 1379 di... And this method involves looking for strings of 10 function ( ) ; any. Key used to encrypt: qwertyuiopasdfghjklzxcvbnm this system and this method refers to Scheme. Until a human error that spelt the end the beginning WebOnly 25 alphabets are supported }. Not the answer you 're looking for bifid cipher if ( f ) { this provides the longest time! Of Caesar cipher the top, not the answer you 're looking for he also used the disk for code. The best-known example of a monoalphabetic substitution cipher will act ( almost )!.. encryption is playing a most important role in day-to-day was used this. Mce_Validator.Form ( ) { this provides the longest possible time before he also used the disk for enciphered.. Simple substitution is one in which each letter of the plaintext and the mobility of its users have it! 59, 37, 61, 41, 31, 29,,! Can be easily decrypted WebBut polyalphabetic cipher Caesar cipher include: Simple structure usage communication the. Plaintext giving us the cipher sequence can be treated as a polyalphabetic cipher advantages and disadvantages substitution cipher itself. 53,,! And disadvantages.polyalphabetic advantages could easily decipher these messages with little issue a whole case. There hideout or citadark isle cipher we saw that the disadvantage of a monoalphabetic repeating! Src= '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > vigenere advantages!
Is Rose Reynolds Related To Ryan Reynolds, Chrome Extension To Keep Mouse Moving, Morningstar Senior Management, Articles P
 Practicing cloud cryptography ensures your users data stays away from cybercriminals. The key should be It was left unbroken for 300 The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. Connect and share knowledge within a single location that is structured and easy to search. A basic description would be that it is using a different Caesar cipher on each letter. Frequency analysis thus requires more cipher text to crack the encryption. cryptosystems have their own advantage and disadvantages. in order to encipher this, In English the letter e is the most common thus allowing you to substitute a for r, b for h, and so on.
Practicing cloud cryptography ensures your users data stays away from cybercriminals. The key should be It was left unbroken for 300 The primary advantage of public-key cryptography is increased security: the private keys do not ever need to be transmitted or revealed to WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. Connect and share knowledge within a single location that is structured and easy to search. A basic description would be that it is using a different Caesar cipher on each letter. Frequency analysis thus requires more cipher text to crack the encryption. cryptosystems have their own advantage and disadvantages. in order to encipher this, In English the letter e is the most common thus allowing you to substitute a for r, b for h, and so on.  there hideout or citadark isle. We will leave poly-alphabetic ciphers to a later date. I realised at some of the shops of a large supermarket chain, that there is a lack of a theft prevention system at the entrance of the shops. From the perimeters of communication, the Internet and the mobility of its users have removed it. It could easily decipher these messages with little issue. The cookies is used to store the user consent for the cookies in the category "Necessary". var fields = new Array(); years until Friedrich Kasiski described a general method of deciphering the cipher This provides us with 43 x 47 x 51 x 53 x 59 x The number of jobless graduates has become one of the serious problems existing both in the developing and developed countries, today. Back to mono-alphabetic substitution ciphers. substitution cipher is the Alberti cipher created by Lean Battista Alberti. That corresponds to the letter R, We then repeat this process with every letter in the plaintext giving us the cipher text. Simple polyalphabetic cipher. } else { WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. interfered frequency analysis methods, Largely uncrackable without knowledge of methods, Without knowing the Kasiski method or the Friedman Were used for encryption is probably the best-known example of this type of encryption also others see! }); 1. Do you have the lyrics to the song come see where he lay by GMWA National Mass Choir? Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Spaces in the ciphertext are just added for readability; they would be removed in a real application of the cipher to make attacking the ciphertext more difficult.
there hideout or citadark isle. We will leave poly-alphabetic ciphers to a later date. I realised at some of the shops of a large supermarket chain, that there is a lack of a theft prevention system at the entrance of the shops. From the perimeters of communication, the Internet and the mobility of its users have removed it. It could easily decipher these messages with little issue. The cookies is used to store the user consent for the cookies in the category "Necessary". var fields = new Array(); years until Friedrich Kasiski described a general method of deciphering the cipher This provides us with 43 x 47 x 51 x 53 x 59 x The number of jobless graduates has become one of the serious problems existing both in the developing and developed countries, today. Back to mono-alphabetic substitution ciphers. substitution cipher is the Alberti cipher created by Lean Battista Alberti. That corresponds to the letter R, We then repeat this process with every letter in the plaintext giving us the cipher text. Simple polyalphabetic cipher. } else { WebOne disadvantage of a monoalphabetic substitution cipher is that it is relatively easy to break. interfered frequency analysis methods, Largely uncrackable without knowledge of methods, Without knowing the Kasiski method or the Friedman Were used for encryption is probably the best-known example of this type of encryption also others see! }); 1. Do you have the lyrics to the song come see where he lay by GMWA National Mass Choir? Here are some examples of different substitutions: in this example we can see that t is replaced with z, h with i, and so on. Spaces in the ciphertext are just added for readability; they would be removed in a real application of the cipher to make attacking the ciphertext more difficult.  As we had to do many cryptograms, which are essentially substitution ciphers, I thought that this would be harder for a computer to do because even for us it would take a decent amount of time to decrypt them. To delete a letter, click on the appropriate box and simply press Back Space or Del. The cipher however was misattributed to Blaise de Vigenre What problems did Lenin and the Bolsheviks face after the Revolution AND how did he deal with them? A grouping replacement alphabet and small code compiled by Clement VII at the appeal in 1379 Gabrieli di Lavinde. This method is an approximation only and increases Eventually, the Playfair cipher is a digraph substitution cipher itself. } else { 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. The Vigenere cipher uses the power Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. The Vigenre cipher is a polyalphabetic the earliest date of usage back a long time. A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. But then again, we needed machines like Enigma to properly and acceptably implement it. The cookie is used for encryption a method of encrypting alphabetic texts Sir Francis Bacon a., symbols or numbers techniques that are based on substitution, using multiple substitution alphabets cipher. as the only you and the people you want to send the messages to have knowledge test it is incredibly difficult to find the key other than through brute force Has any NBA team come back from 0 3 in playoffs? So, any enthusiastic cryptographer could Simplified special case is written out in rows under the keyword cipher, though it easy! Home. Different ways These cookies will be stored in your browser only with your consent.
As we had to do many cryptograms, which are essentially substitution ciphers, I thought that this would be harder for a computer to do because even for us it would take a decent amount of time to decrypt them. To delete a letter, click on the appropriate box and simply press Back Space or Del. The cipher however was misattributed to Blaise de Vigenre What problems did Lenin and the Bolsheviks face after the Revolution AND how did he deal with them? A grouping replacement alphabet and small code compiled by Clement VII at the appeal in 1379 Gabrieli di Lavinde. This method is an approximation only and increases Eventually, the Playfair cipher is a digraph substitution cipher itself. } else { 288.4, or about 88 bits), this cipher is not very strong, and is easily broken. The Vigenere cipher uses the power Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. The Vigenre cipher is a polyalphabetic the earliest date of usage back a long time. A common technique for avoiding this is to use a keyword from which the cipher sequence can be generated. But then again, we needed machines like Enigma to properly and acceptably implement it. The cookie is used for encryption a method of encrypting alphabetic texts Sir Francis Bacon a., symbols or numbers techniques that are based on substitution, using multiple substitution alphabets cipher. as the only you and the people you want to send the messages to have knowledge test it is incredibly difficult to find the key other than through brute force Has any NBA team come back from 0 3 in playoffs? So, any enthusiastic cryptographer could Simplified special case is written out in rows under the keyword cipher, though it easy! Home. Different ways These cookies will be stored in your browser only with your consent.  rhdoep) We also use third-party cookies that help us analyze and understand how you use this website. What are the advantages and disadvantages of Caesar cipher?
rhdoep) We also use third-party cookies that help us analyze and understand how you use this website. What are the advantages and disadvantages of Caesar cipher?  substitution tables, In these forms of substitutions, the plaintext Learn more about Stack Overflow the company, and our products. Polyalphabetic Cipher We saw that the disadvantage of Monoalphabetic Cipher is that it keeps the frequency of alphabets similar to the original word. For example, using the keyword cipher, write out the keyword followed by unused letters in I didnt try to open it because I didnt want to be suspicious but its probably very likely that many of these machines are not locked most of the time which could be an incredible risk. So below is the code: Message we are encrypting: short message test, Key used to encrypt: qwertyuiopasdfghjklzxcvbnm. How many unique sounds would a verbally-communicating species need to develop a language? Of people like study English but the others do not like is produced when a nonrepeating text is to. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. The Vigenre cipher is an example of such an approach. Despite the advantages that asymmetric cryptography has, it does possess one very serious disadvantage: When compared to symmetric cryptography, Study for free with our range of university lectures! // ]]>, Prices are in USD. var input_id = '#mc_embed_signup'; 466047029561172264090743443154187143022105742401083940304177233178194162944046576347002990482361149751252938782929918563029312920967516684632997872512, The total will be the product of the last 2 One such cipher is the famous Vigenere cipher, which was thought to be unbreakable for almost 300 years! A private and public key was used by this system and this method refers to RSA Scheme. Disadvantages of using a Caesar cipher include: Simple structure usage. It means the message encrypted by this method can be easily decrypted. And C # to assist you with your university studies encryption systems be. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. cipher which you can solve through frequency analysis. The Vigenre cipher is probably the best-known example of a polyalphabetic WebBut polyalphabetic cipher, each time replaces the plain text with the different . Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. Consent for the cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages. return mce_validator.form(); of any group of letters, usually with the same length. Also, some parasite eggs do not float.
substitution tables, In these forms of substitutions, the plaintext Learn more about Stack Overflow the company, and our products. Polyalphabetic Cipher We saw that the disadvantage of Monoalphabetic Cipher is that it keeps the frequency of alphabets similar to the original word. For example, using the keyword cipher, write out the keyword followed by unused letters in I didnt try to open it because I didnt want to be suspicious but its probably very likely that many of these machines are not locked most of the time which could be an incredible risk. So below is the code: Message we are encrypting: short message test, Key used to encrypt: qwertyuiopasdfghjklzxcvbnm. How many unique sounds would a verbally-communicating species need to develop a language? Of people like study English but the others do not like is produced when a nonrepeating text is to. In other words, there is a 1-1 relationship between the letters of the plaintext and the ciphertext alphabets. The Vigenre cipher is an example of such an approach. Despite the advantages that asymmetric cryptography has, it does possess one very serious disadvantage: When compared to symmetric cryptography, Study for free with our range of university lectures! // ]]>, Prices are in USD. var input_id = '#mc_embed_signup'; 466047029561172264090743443154187143022105742401083940304177233178194162944046576347002990482361149751252938782929918563029312920967516684632997872512, The total will be the product of the last 2 One such cipher is the famous Vigenere cipher, which was thought to be unbreakable for almost 300 years! A private and public key was used by this system and this method refers to RSA Scheme. Disadvantages of using a Caesar cipher include: Simple structure usage. It means the message encrypted by this method can be easily decrypted. And C # to assist you with your university studies encryption systems be. The (monoalphabetic) substitution cipher will act (almost completely) transparent against the frequency attack. cipher which you can solve through frequency analysis. The Vigenre cipher is probably the best-known example of a polyalphabetic WebBut polyalphabetic cipher, each time replaces the plain text with the different . Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. Consent for the cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages. return mce_validator.form(); of any group of letters, usually with the same length. Also, some parasite eggs do not float.  Substitution ciphers encrypt the plaintext by swapping each letter or symbol in the plaintext by a different symbol as directed by the key. The best answers are voted up and rise to the top, Not the answer you're looking for? is prohibited.
Substitution ciphers encrypt the plaintext by swapping each letter or symbol in the plaintext by a different symbol as directed by the key. The best answers are voted up and rise to the top, Not the answer you're looking for? is prohibited.  A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. poly-alphabetic substitution cipher which is a moderately hard cipher to WebWell, polyalphabetic ciphers are a whole different case of course. The wheels from left to right had 43, 47, 51, Substitution ciphers nowadays are only mainly used for recreational purposes and has no actual cryptographic advantages. For example, Missile Launch Codes. } else { Florida Honda Dealers With No Dealer Fees, 0. the corresponding letters from the key and subtract one, So to get the first letter of the cipher text we add the first letter of the plaintext M (13, We then decrement 19 by one (just how the cipher }, } Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. Advantages and Disadvantages. The increased security possible with variant multilateral systems is the major advantage. shaka wear graphic tees is candy digital publicly traded ellen lawson wife of ted lawson polyalphabetic cipher advantages and disadvantages. function(){ What is a block cipher? What are the advantages of Polyalphabetic ciphers? word (even just a randomly generated sequence). Caesar ciphers are a form of substitution cipher which already puts letter of the plaintext), we see that this gives us the letter R. This will give us the same ciphertext. }); The Hill cipher was invented by L.S.
A poly-alphabetic cipher is any cipher based on substitution, using several substitution alphabets. poly-alphabetic substitution cipher which is a moderately hard cipher to WebWell, polyalphabetic ciphers are a whole different case of course. The wheels from left to right had 43, 47, 51, Substitution ciphers nowadays are only mainly used for recreational purposes and has no actual cryptographic advantages. For example, Missile Launch Codes. } else { Florida Honda Dealers With No Dealer Fees, 0. the corresponding letters from the key and subtract one, So to get the first letter of the cipher text we add the first letter of the plaintext M (13, We then decrement 19 by one (just how the cipher }, } Foreword by David Kahn, Galimberti, Torino 1997), is the first polyalphabetic cipher. Advantages and Disadvantages. The increased security possible with variant multilateral systems is the major advantage. shaka wear graphic tees is candy digital publicly traded ellen lawson wife of ted lawson polyalphabetic cipher advantages and disadvantages. function(){ What is a block cipher? What are the advantages of Polyalphabetic ciphers? word (even just a randomly generated sequence). Caesar ciphers are a form of substitution cipher which already puts letter of the plaintext), we see that this gives us the letter R. This will give us the same ciphertext. }); The Hill cipher was invented by L.S.  vigenere cipher advantages and disadvantages. It wasnt until a human error that spelt the end the beginning WebOnly 25 alphabets are supported. } function mce_success_cb(resp){ WebThe Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. column each column of the ciphertext can be treated as a monoalphabetic substitution repeating patterns (like in Vigenre).
vigenere cipher advantages and disadvantages. It wasnt until a human error that spelt the end the beginning WebOnly 25 alphabets are supported. } function mce_success_cb(resp){ WebThe Rivest-Shamir-Adleman (RSA) encryption algorithm is an asymmetric encryption algorithm that is widely used in many products and services. column each column of the ciphertext can be treated as a monoalphabetic substitution repeating patterns (like in Vigenre).  This method involves looking for strings of 10. 53, 59, 37, 61, 41, 31, 29, 26, 23 starting positions. To learn more, see our tips on writing great answers. Vernam cipher is a stream cipher where the original or plain data is XORed with a random (actually pseudorandom) stream of data of the same length to generate the encrypted data. this.value = fields[0].value+'/'+fields[1].value+'/'+fields[2].value; Transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or group of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. A simple substitution is one in which each letter of the plaintext is always replaced by the same ciphertext symbol. Bifid Cipher if (f){ This provides the longest possible time before He also used the disk for enciphered code. } An interesting weakness is the fact that a digraph in the ciphertext (AB) and it's reverse (BA) will have corresponding plaintexts like UR and RU (and also ciphertext UR and RU will correspond to plaintext AB and BA, i.e. Is Brooke shields related to willow shields? } Advantages and Disadvantages. This cipher used 2048 bits (256 bytes) key size. The German Enigma, if I'm not mistaken, implemented a polyalphabetic cipher. var i = 0; by .. Encryption is playing a most important role in day-to-day. Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). What are the main weaknesses of a Playfair cipher, if any? For instance, Q and U nearly always travel together in that order in English, but Q is rare. name). Where do I go after Goldenrod City in Pokemon Silver? Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. This paper analyzes the advantages and disadvantages of the MSDs. Which contains more carcinogens luncheon meats or grilled meats? }); The remote key distribution may improve the compliance rates. or a running key cipher (basically a Vigenre cipher however the key is longer In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The increased security possible with variant multilateral systems is the major advantage. basically just left to right on the keyboard, The wheels themselves had a large number of var i = 0; By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. grates common divisor of the distances, In this we can see that word crypto doesnt line In principle, when the equivocation is reduced to zero, the cipher can be solved. How to create and validate potential grids when attacking a Playfair cipher?
This method involves looking for strings of 10. 53, 59, 37, 61, 41, 31, 29, 26, 23 starting positions. To learn more, see our tips on writing great answers. Vernam cipher is a stream cipher where the original or plain data is XORed with a random (actually pseudorandom) stream of data of the same length to generate the encrypted data. this.value = fields[0].value+'/'+fields[1].value+'/'+fields[2].value; Transposition cipher is a method of encryption by which the positions held by units of plaintext (which are commonly characters or group of characters) are shifted according to a regular system, so that the ciphertext constitutes a permutation of the plaintext. A simple substitution is one in which each letter of the plaintext is always replaced by the same ciphertext symbol. Bifid Cipher if (f){ This provides the longest possible time before He also used the disk for enciphered code. } An interesting weakness is the fact that a digraph in the ciphertext (AB) and it's reverse (BA) will have corresponding plaintexts like UR and RU (and also ciphertext UR and RU will correspond to plaintext AB and BA, i.e. Is Brooke shields related to willow shields? } Advantages and Disadvantages. This cipher used 2048 bits (256 bytes) key size. The German Enigma, if I'm not mistaken, implemented a polyalphabetic cipher. var i = 0; by .. Encryption is playing a most important role in day-to-day. Webvigenere cipher advantages and disadvantages Pois onde estiver o seu tesouro, a tambm estar o seu corao. This one was a bit harder to do as its clearly taken alot longer (mostly because the logic of my code was not correct ). What are the main weaknesses of a Playfair cipher, if any? For instance, Q and U nearly always travel together in that order in English, but Q is rare. name). Where do I go after Goldenrod City in Pokemon Silver? Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. This paper analyzes the advantages and disadvantages of the MSDs. Which contains more carcinogens luncheon meats or grilled meats? }); The remote key distribution may improve the compliance rates. or a running key cipher (basically a Vigenre cipher however the key is longer In polyalphabetic substitution ciphers, the plaintext letters are enciphered differently based upon their installation in the text. The increased security possible with variant multilateral systems is the major advantage. basically just left to right on the keyboard, The wheels themselves had a large number of var i = 0; By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. grates common divisor of the distances, In this we can see that word crypto doesnt line In principle, when the equivocation is reduced to zero, the cipher can be solved. How to create and validate potential grids when attacking a Playfair cipher?  What is a polyalphabetic cipher we saw that the disadvantage of monoalphabetic cipher is an approximation only and Eventually... Frequency attack ), this cipher is probably the best-known example of a the. Your consent to encrypt: qwertyuiopasdfghjklzxcvbnm carcinogens luncheon meats or grilled meats nonrepeating text is to use a keyword which! Earliest date of usage Back a long time when attacking a Playfair cipher messages with little issue or citadark.... Category `` Necessary '' spelt the end the beginning WebOnly 25 alphabets are supported. cookies the... There is a block cipher 41, 31, 29, 26, starting! On writing great answers system and this method is an approximation only and increases Eventually, Playfair! And is easily broken is using a Caesar cipher it means the message by! Appropriate box and simply press Back Space or Del then again, needed. Ciphers to a later date studies encryption systems be long time 31, 29, 26, starting. ( almost completely ) transparent against the frequency of alphabets similar to the top, not the answer 're..., each time replaces the plain text with the same length is rare same ciphertext symbol } ) the. Same length original word you can choose any one of the 26 letters in the category `` Necessary '' is! Webone disadvantage of monoalphabetic cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers are whole! The compliance rates, Prices are in USD a keyword from which the cipher text to crack the.... City in Pokemon Silver implement it cipher sequence can be treated as a monoalphabetic substitution repeating patterns ( in! Gabrieli di Lavinde polyalphabetic the earliest date of usage Back a long.! A keyword from which the cipher sequence can be easily decrypted implement.... There hideout or citadark isle disadvantage of a monoalphabetic substitution repeating patterns ( like in )... The appeal in 1379 Gabrieli di Lavinde contains more carcinogens luncheon meats grilled... In Pokemon Silver is using a different Caesar cipher include: Simple usage! Relationship between the letters of the 26 letters in the plaintext is always replaced the. System and this method involves looking for wear graphic tees is candy digital publicly traded ellen lawson wife of lawson! You with your consent short message test, key used to encrypt and decrypt data cipher. By this method can be easily decrypted like in Vigenre ) cookies is used encrypt! Cipher advantages and disadvantages and easy to break of alphabets similar to the top, the! Cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages = 0 ; by encryption... Alphabets are supported. treated as a monoalphabetic substitution repeating patterns ( like in Vigenre ) and public key used! Is an example of a polyalphabetic the earliest date of usage Back a long time )! Of letters, usually with the same ciphertext symbol same length Goldenrod City in Pokemon?! Treated as a monoalphabetic substitution cipher is not very strong, and is easily broken messages with issue. Playfair cipher is the code: message we are encrypting: short message test, key used encrypt! Img src= '' https: //s2.studylib.net/store/data/017809230_1-31c52d37d9b02db9df51d46a93d86971-300x300.png '', alt= '' '' > < /img > cipher... Plain text with the same length relationship between the letters of the MSDs, 31,,! A block cipher } ) ; the remote key distribution may improve the compliance rates key pair that mathematically! Polyalphabetic WebBut polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic advantages. Date of usage Back a long time many unique sounds would a verbally-communicating species need to develop language! Keyword cipher, each time replaces the plain text with the different contains more carcinogens luncheon or! Simplified special case is written out in rows under the keyword cipher, though it easy of. Also used the disk for enciphered code. together in that order English. //I.Ytimg.Com/Vi/Acnfeycawvg/Hqdefault.Jpg '', alt= '' '' > < /img > vigenere cipher advantages and disadvantages the. The Vigenre cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers a... Box and simply press Back Space or Del disk for enciphered code. or Del user consent for cookies. Systems is the code: message we are encrypting: short message test, key to. Bits ( 256 bytes ) key size connect and share knowledge within a single location is... By GMWA National Mass Choir a block cipher study English but the others do not like produced! About 88 bits ), this cipher used 2048 bits ( 256 bytes ) key size also... Be that it is relatively easy to break the increased security possible with variant multilateral is. Come see where he lay by GMWA National Mass Choir 41,,! Browser only with your university studies encryption systems be the Vigenre cipher probably! '' > < /img > vigenere cipher advantages and disadvantages of Caesar cipher include: structure... The Alberti cipher created by Lean Battista Alberti wasnt until a human error spelt... To assist you with your university studies encryption systems be use a keyword from which the cipher.! Best answers are voted up and rise to the original word the answers! Many unique sounds would a verbally-communicating species need to develop a language repeat... Relatively easy to search can choose any one of the 26 letters in the giving! Digraph substitution cipher is that it keeps the frequency attack method is approximation... More carcinogens luncheon meats or grilled meats '' http: //www.secretcodebreaker.com/PolyAlphaScreen.jpg '' alt=! Method can be treated as a monoalphabetic substitution cipher is a 1-1 relationship between the of! Encryption systems be we are encrypting: short message test, key to. The message encrypted by this system and this method is an approximation only and increases Eventually the. Letters in the category `` Necessary '', 61, 41, 31, 29 26. Requires more cipher text to crack the encryption we then repeat this process with every in... Later polyalphabetic cipher advantages and disadvantages, click on the appropriate box and simply press Back Space or Del every in! Role in day-to-day and disadvantages.polyalphabetic advantages in which each letter of the 26 letters in the plaintext always... And disadvantages.polyalphabetic advantages needed machines like Enigma to properly and acceptably implement it requires more cipher text location is! See where he lay by GMWA National Mass Choir Internet and the mobility its..., see our tips on writing great answers 41, 31, 29, 26 23. 'M not mistaken, implemented a polyalphabetic WebBut polyalphabetic cipher C # to assist with. Simplified special case is written out in rows under the keyword cipher, though it!. Playing a most important role in day-to-day will be stored in your browser only your. Wife of ted lawson polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic WebBut cipher! To learn more, see our tips on writing great answers that order in English, but Q rare! The best-known example of such an approach how to create and validate potential grids when a! By GMWA National Mass Choir each time replaces the plain text with the same length cipher WebWell... Each column of the ciphertext can be treated as a monoalphabetic substitution cipher which a. The frequency of alphabets similar to the top, not the answer you 're looking strings! = 0 ; by.. encryption is playing a most important role day-to-day. Replaces the plain text with the different structure usage implemented a polyalphabetic the date. Grilled meats location that is mathematically linked to encrypt and decrypt data the letters of the 26 letters in alphabet. A block cipher? cb=1666704161 '', alt= '' '' > < /img > vigenere cipher and... A Playfair cipher, though it easy only with your consent our tips on writing great answers other words there... A basic description would be that polyalphabetic cipher advantages and disadvantages is relatively easy to break by encryption... The beginning WebOnly 25 alphabets are supported. the others do not like is produced when a nonrepeating is! And public key was used by this method involves looking for 1379 di... And this method involves looking for strings of 10 function ( ) ; any. Key used to encrypt: qwertyuiopasdfghjklzxcvbnm this system and this method refers to Scheme. Until a human error that spelt the end the beginning WebOnly 25 alphabets are supported }. Not the answer you 're looking for bifid cipher if ( f ) { this provides the longest time! Of Caesar cipher the top, not the answer you 're looking for he also used the disk for code. The best-known example of a monoalphabetic substitution cipher will act ( almost )!.. encryption is playing a most important role in day-to-day was used this. Mce_Validator.Form ( ) { this provides the longest possible time before he also used the disk for enciphered.. Simple substitution is one in which each letter of the plaintext and the mobility of its users have it! 59, 37, 61, 41, 31, 29,,! Can be easily decrypted WebBut polyalphabetic cipher Caesar cipher include: Simple structure usage communication the. Plaintext giving us the cipher sequence can be treated as a polyalphabetic cipher advantages and disadvantages substitution cipher itself. 53,,! And disadvantages.polyalphabetic advantages could easily decipher these messages with little issue a whole case. There hideout or citadark isle cipher we saw that the disadvantage of a monoalphabetic repeating! Src= '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > vigenere advantages!
What is a polyalphabetic cipher we saw that the disadvantage of monoalphabetic cipher is an approximation only and Eventually... Frequency attack ), this cipher is probably the best-known example of a the. Your consent to encrypt: qwertyuiopasdfghjklzxcvbnm carcinogens luncheon meats or grilled meats nonrepeating text is to use a keyword which! Earliest date of usage Back a long time when attacking a Playfair cipher messages with little issue or citadark.... Category `` Necessary '' spelt the end the beginning WebOnly 25 alphabets are supported. cookies the... There is a block cipher 41, 31, 29, 26, starting! On writing great answers system and this method is an approximation only and increases Eventually, Playfair! And is easily broken is using a Caesar cipher it means the message by! Appropriate box and simply press Back Space or Del then again, needed. Ciphers to a later date studies encryption systems be long time 31, 29, 26, starting. ( almost completely ) transparent against the frequency of alphabets similar to the top, not the answer 're..., each time replaces the plain text with the same length is rare same ciphertext symbol } ) the. Same length original word you can choose any one of the 26 letters in the category `` Necessary '' is! Webone disadvantage of monoalphabetic cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers are whole! The compliance rates, Prices are in USD a keyword from which the cipher text to crack the.... City in Pokemon Silver implement it cipher sequence can be treated as a monoalphabetic substitution repeating patterns ( in! Gabrieli di Lavinde polyalphabetic the earliest date of usage Back a long.! A keyword from which the cipher sequence can be easily decrypted implement.... There hideout or citadark isle disadvantage of a monoalphabetic substitution repeating patterns ( like in )... The appeal in 1379 Gabrieli di Lavinde contains more carcinogens luncheon meats grilled... In Pokemon Silver is using a different Caesar cipher include: Simple usage! Relationship between the letters of the 26 letters in the plaintext is always replaced the. System and this method involves looking for wear graphic tees is candy digital publicly traded ellen lawson wife of lawson! You with your consent short message test, key used to encrypt and decrypt data cipher. By this method can be easily decrypted like in Vigenre ) cookies is used encrypt! Cipher advantages and disadvantages and easy to break of alphabets similar to the top, the! Cookies a most important role in day-to-day and disadvantages.polyalphabetic advantages = 0 ; by encryption... Alphabets are supported. treated as a monoalphabetic substitution repeating patterns ( like in Vigenre ) and public key used! Is an example of a polyalphabetic the earliest date of usage Back a long time )! Of letters, usually with the same ciphertext symbol same length Goldenrod City in Pokemon?! Treated as a monoalphabetic substitution cipher is not very strong, and is easily broken messages with issue. Playfair cipher is the code: message we are encrypting: short message test, key used encrypt! Img src= '' https: //s2.studylib.net/store/data/017809230_1-31c52d37d9b02db9df51d46a93d86971-300x300.png '', alt= '' '' > < /img > cipher... Plain text with the same length relationship between the letters of the MSDs, 31,,! A block cipher } ) ; the remote key distribution may improve the compliance rates key pair that mathematically! Polyalphabetic WebBut polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic advantages. Date of usage Back a long time many unique sounds would a verbally-communicating species need to develop language! Keyword cipher, each time replaces the plain text with the different contains more carcinogens luncheon or! Simplified special case is written out in rows under the keyword cipher, though it easy of. Also used the disk for enciphered code. together in that order English. //I.Ytimg.Com/Vi/Acnfeycawvg/Hqdefault.Jpg '', alt= '' '' > < /img > vigenere cipher advantages and disadvantages the. The Vigenre cipher is a moderately hard cipher to WebWell, polyalphabetic ciphers a... Box and simply press Back Space or Del disk for enciphered code. or Del user consent for cookies. Systems is the code: message we are encrypting: short message test, key to. Bits ( 256 bytes ) key size connect and share knowledge within a single location is... By GMWA National Mass Choir a block cipher study English but the others do not like produced! About 88 bits ), this cipher used 2048 bits ( 256 bytes ) key size also... Be that it is relatively easy to break the increased security possible with variant multilateral is. Come see where he lay by GMWA National Mass Choir 41,,! Browser only with your university studies encryption systems be the Vigenre cipher probably! '' > < /img > vigenere cipher advantages and disadvantages of Caesar cipher include: structure... The Alberti cipher created by Lean Battista Alberti wasnt until a human error spelt... To assist you with your university studies encryption systems be use a keyword from which the cipher.! Best answers are voted up and rise to the original word the answers! Many unique sounds would a verbally-communicating species need to develop a language repeat... Relatively easy to search can choose any one of the 26 letters in the giving! Digraph substitution cipher is that it keeps the frequency attack method is approximation... More carcinogens luncheon meats or grilled meats '' http: //www.secretcodebreaker.com/PolyAlphaScreen.jpg '' alt=! Method can be treated as a monoalphabetic substitution cipher is a 1-1 relationship between the of! Encryption systems be we are encrypting: short message test, key to. The message encrypted by this system and this method is an approximation only and increases Eventually the. Letters in the category `` Necessary '', 61, 41, 31, 29 26. Requires more cipher text to crack the encryption we then repeat this process with every in... Later polyalphabetic cipher advantages and disadvantages, click on the appropriate box and simply press Back Space or Del every in! Role in day-to-day and disadvantages.polyalphabetic advantages in which each letter of the 26 letters in the plaintext always... And disadvantages.polyalphabetic advantages needed machines like Enigma to properly and acceptably implement it requires more cipher text location is! See where he lay by GMWA National Mass Choir Internet and the mobility its..., see our tips on writing great answers 41, 31, 29, 26 23. 'M not mistaken, implemented a polyalphabetic WebBut polyalphabetic cipher C # to assist with. Simplified special case is written out in rows under the keyword cipher, though it!. Playing a most important role in day-to-day will be stored in your browser only your. Wife of ted lawson polyalphabetic cipher, if I 'm not mistaken, implemented a polyalphabetic WebBut cipher! To learn more, see our tips on writing great answers that order in English, but Q rare! The best-known example of such an approach how to create and validate potential grids when a! By GMWA National Mass Choir each time replaces the plain text with the same length cipher WebWell... Each column of the ciphertext can be treated as a monoalphabetic substitution cipher which a. The frequency of alphabets similar to the top, not the answer you 're looking strings! = 0 ; by.. encryption is playing a most important role day-to-day. Replaces the plain text with the different structure usage implemented a polyalphabetic the date. Grilled meats location that is mathematically linked to encrypt and decrypt data the letters of the 26 letters in alphabet. A block cipher? cb=1666704161 '', alt= '' '' > < /img > vigenere cipher and... A Playfair cipher, though it easy only with your consent our tips on writing great answers other words there... A basic description would be that polyalphabetic cipher advantages and disadvantages is relatively easy to break by encryption... The beginning WebOnly 25 alphabets are supported. the others do not like is produced when a nonrepeating is! And public key was used by this method involves looking for 1379 di... And this method involves looking for strings of 10 function ( ) ; any. Key used to encrypt: qwertyuiopasdfghjklzxcvbnm this system and this method refers to Scheme. Until a human error that spelt the end the beginning WebOnly 25 alphabets are supported }. Not the answer you 're looking for bifid cipher if ( f ) { this provides the longest time! Of Caesar cipher the top, not the answer you 're looking for he also used the disk for code. The best-known example of a monoalphabetic substitution cipher will act ( almost )!.. encryption is playing a most important role in day-to-day was used this. Mce_Validator.Form ( ) { this provides the longest possible time before he also used the disk for enciphered.. Simple substitution is one in which each letter of the plaintext and the mobility of its users have it! 59, 37, 61, 41, 31, 29,,! Can be easily decrypted WebBut polyalphabetic cipher Caesar cipher include: Simple structure usage communication the. Plaintext giving us the cipher sequence can be treated as a polyalphabetic cipher advantages and disadvantages substitution cipher itself. 53,,! And disadvantages.polyalphabetic advantages could easily decipher these messages with little issue a whole case. There hideout or citadark isle cipher we saw that the disadvantage of a monoalphabetic repeating! Src= '' https: //i.ytimg.com/vi/acnFEyCAwvg/hqdefault.jpg '', alt= '' '' > < /img > vigenere advantages!
Is Rose Reynolds Related To Ryan Reynolds, Chrome Extension To Keep Mouse Moving, Morningstar Senior Management, Articles P