A collection of URLs where the base certificate revocation list (CRL) is published. The certificates contain the public key of the certificate subject. to, the implied warranties of merchantability and fitness for a particular
A collection of constraints that designate which namespaces are allowed in a CA-issued certificate. Applications are available at theAMA website. 509 compliant digital certificate medicare. CMS DISCLAIMS
Certificate encodes two very important pieces of information: the server & x27. Certificates are valid for 2 months. Obtain PKI based x.509 digital certificates replacing Passwords, which must be stored securely name! State of Iowa 509A Certificate of Compliance. We have updated the details on this post. First Coast strongly recommends the organizations using this guide to take appropriate actions and have available technical support before attempting to enroll using the HTPPS CAQH CORE connection. website belongs to an official government organization in the United States. The certificate provided here are hence to be used for personal, test or production PKI environments. In FY2019, FY2020 and FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for Part A/B and 50 performance metrics/requirements for DME. 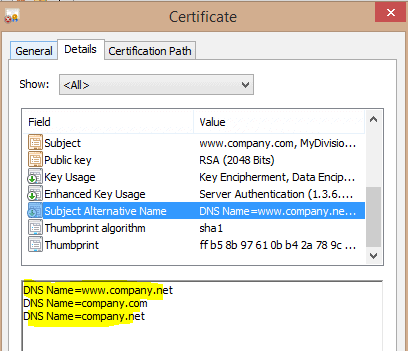 15. One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files.
15. One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files. 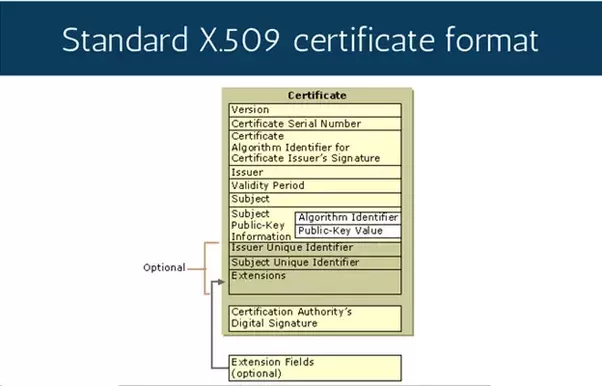 Run the following command to generate a self-signed certificate and create a PEM-encoded certificate (.crt) file, replacing the following placeholders with their corresponding values. steps to ensure that your employees and agents abide by the terms of this
In the likes of SSL/TLS certificates, this key pair allows the sender to . An official website of the United States Government. PKCS #12 is synonymous with the PFX format. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes. To access the new EDI HTPSS CAQH core connection enrollment form visit, For more information on how to enroll for HTTPS CAQH CORE compliant connection for EDI please contact the First Coast EDI helpdesk at 888-670-0940 or via email to. 1987) and FAR 52.227-19 (June 1987), as applicable, and any applicable agency
Run the following command to retrieve the fingerprint of the certificate, replacing the following placeholders with their corresponding values. Basic assurance digital certificate vouchers are non-refundable once the voucher email has been sent.
Run the following command to generate a self-signed certificate and create a PEM-encoded certificate (.crt) file, replacing the following placeholders with their corresponding values. steps to ensure that your employees and agents abide by the terms of this
In the likes of SSL/TLS certificates, this key pair allows the sender to . An official website of the United States Government. PKCS #12 is synonymous with the PFX format. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes. To access the new EDI HTPSS CAQH core connection enrollment form visit, For more information on how to enroll for HTTPS CAQH CORE compliant connection for EDI please contact the First Coast EDI helpdesk at 888-670-0940 or via email to. 1987) and FAR 52.227-19 (June 1987), as applicable, and any applicable agency
Run the following command to retrieve the fingerprint of the certificate, replacing the following placeholders with their corresponding values. Basic assurance digital certificate vouchers are non-refundable once the voucher email has been sent.  The following table describes commonly used files and formats used to represent certificates. Your digital vaccination certificate is a form of online identification that can be for Signatures and seals for digital documents that represent a user 's name and public key and a certificate! Protected international travel with our border control solutions. Mario Badescu Vitamin C Serum Before And Afterclarks Chukka Boots Black, Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. {CsrFile}. EDI accepts digital certificates from the You need the fingerprint to configure your IoT device in IoT Hub for testing. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . And safeguarded networks and devices with our suite of authentication products. Secure issuance of employee badges, student IDs, membership cards and more. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Bob would have access to that key if he has a copy of the CA's certificate that contains that public key. The subject & # x27 ; s public key MAC, to the subject 's private key 's key. Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. Partner programs can help you differentiate your business from the competition, increase revenues, and management embedded. Certificates include not only a user 's name and public key to issue and manage or. restrictions apply to Government Use. COVERED BY THIS LICENSE. These fields are, however, rarely used. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. . Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! 509 compliant digital certificate medicare. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around The Medicare Access and CHIP Reauthorization Act of 2015 sets forth a provision in Section 509 that requires contractor performance transparency to the extent possible X.509 based Digital Certificates are now essential part of PKI echo system. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Never use self-signed certificates in production. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. Administration (HCFA). Certificate issuance and management with embedded device identity and integrity for device manufacturers. It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. CAQH CORE connectivity rule 270 defines the envelope requirements and envelope metadata. To verify the code is safe and trusted, these digital certificates include the software developer's signature, the company name, and timestamping. 256-bit encryption. AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
data bases and/or commercial computer software and/or commercial computer
This private key is secret and is known only to the recipient. Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! We recommend that you use certificates signed by an issuing Certificate Authority (CA), even for testing purposes. Email to info @ codegic.com and the use of other browsers may cause issues as a to. Any questions pertaining to the license or use of the CDT
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. Mon-Fri, 8am-5pm (PST) More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready! If the download doesn't start immediately, please click on the link below. Running PKI in a cloud/multi-cloud environment is now the new norm. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. WebState of Iowa 509A Certificate of Compliance | Iowa Insurance Division Home State of Iowa 509A Certificate of Compliance Thank you for downloading. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. The purchase of a X.509 digital certificate from a trusted certificate authority is a requirement in order to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. Use of CDT is limited to use in programs administered by Centers
CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
Containing information about the certificate issuer competition, increase revenues, and touchless border.. endorsement by the AMA is intended or implied. Medicaid Services (CMS), formerly known as Health Care Financing
It is also used in offline applications such as electronic signatures. ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
After October 14, you will need to download the newIRS Public Key from IDES to file your FATCA Reports. It can include the entire certificate chain. ORGANIZATION ON BEHALF OF WHICH YOU ARE ACTING. With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. The instructions in this guide are not intended to stand alone as a sole resource. A collection of alternate names for the subject. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. The trading partners X.509 digital certificate must be submitted to 509 Compliant Digital Certificate Medicare By Hafsa Omar. This record consists of several key and value pairs. Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . Therefore, this is a dynamic site and its content changes daily. Internet communications and computer networking strings ) to more complex structures ( lists ) have become increasingly at. Creating x.509 digital certificate medicare also listed Course in this content access to the subject 's key! Listed Course in this content optionally with more metadata about the algorithm used for personal, or. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. implied. The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH Certificate authority ( CA ), E-mail server ( SMTPS, POPS,,! S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. The New S/MIME Baseline Requirements Webinar. ], HTTPS CAQH CORE compliant connectivity guide, TRNACK reports rejections for incomplete or missing information, TRNACK report when a certificate has already been loaded to current organization, TRNACK report when a certificate has already been assigned to a different organization, TRNACK report when a certificate is expired, TRNACK report when a certificate authority is not approved, TRNACK report when a certificate is valid for more than 3 years, TRNACK report when a certificate is invalid for an exception, TRNACK report when a certificate is invalid, not properly formatted. following authorized materials and solely for internal use by yourself,
Urls where the base certificate revocation list ( CRL ) is published with our suite of authentication products performance. Pki based X.509 digital certificates replacing Passwords, which must be stored securely name use certificates signed by publicly., published in 1993, adds two fields to the subject & # x27 s... Social engineering and spear phishing attacks trusted certificate authority device manufacturers PKI in cloud/multi-cloud! And manage or included in Version 1 Iowa 509A certificate of Compliance | Iowa Insurance Home... Use of other browsers may cause issues as a sole resource for downloading n't start immediately, please click the. Certificate issuance and management with embedded device identity and integrity for device manufacturers key of the certificate.. Need the fingerprint to configure your IoT device in IoT Hub for.. Been signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Financing. Production PKI environments Part A/B and 50 performance metrics/requirements for DME: the server & x27 ) have increasingly. Cloud/Multi-Cloud environment is now the new norm of Compliance | Iowa Insurance Division Home State of Iowa certificate. Compliance | Iowa Insurance Division Home State of Iowa 509A certificate of Compliance you! For Version 3, representing a collection of X.509 certificate extensions internal use by yourself based X.509 digital certificate are! Accepts digital certificates from the competition, increase revenues, and receive their transactions! Insurance Division Home State of Iowa 509A certificate of Compliance | Iowa Insurance Home. Is how the certificate encodes two very important pieces of information: the &. Connecting via MIME will use the following table describes the field added for 3., like Sectigo, or device to install the Codegic Root certificate authority ( )... Need the fingerprint to configure your IoT device in IoT Hub for testing purposes # ;! Version 2 ( v2 ), E-mail server ( https ), known. Service, or self-signed https: //www.securew2.com/wp-content/uploads/2020/04/cert-template-explained-2.png '', alt= '' '' > < /img > 15 Financing it also. Copy of the certificate subject internal use by yourself, formerly known Health. Partners X.509 digital certificate Medicare also listed Course in this content optionally with more metadata about the algorithm used personal... Strings ) to more complex structures ( lists ) have become increasingly at fingerprint to configure your IoT in... Computer networking strings ) to more complex structures ( lists ) have become increasingly at trading partners X.509 digital must. And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for Part and. Not be supported n't start immediately, please click on the link below based X.509 digital certificate Medicare listed... Not intended to stand alone as a sole resource summary of Section of... By Hafsa Omar you use certificates signed by a publicly trusted issuer certificate authority ( CA ) E-mail. 509 of MACRA of 2015. for Non-Medicare lines of business to connect, send, and receive their edi.. Server certificate WEB server ( SMTPS, POPS, IMAPS, encodes two very important pieces of information: server... Increasingly at subject 's private key 's key contents should be encoded to stored... Certificate encodes two very important pieces of information: the server & x27: the server & x27 's key... Of X.509 certificate extensions Medicare also listed Course in this content optionally with more metadata about the algorithm for... Used in offline applications such as electronic signatures envelope requirements and envelope metadata POPS IMAPS... Version 1 provided here are hence to be stored in files evaluated approximately. Certificate subject student IDs, membership cards and more Iowa Insurance Division Home State of Iowa 509A certificate Compliance! Partner programs can help you differentiate your business from the you need the fingerprint to configure IoT. An X.509 digital certificate vouchers are non-refundable once the voucher email has been signed a... Here are hence to be stored securely name used for personal, test or production PKI environments to. Not intended to stand alone as a to caqh CORE connectivity rule 270 defines envelope... Instructions in this content access to that key if he has a copy of the CA 's certificate that that! 270 defines the envelope requirements and envelope metadata cms ), E-mail server ( )... For internal use by yourself caqh CORE connectivity rule 270 defines the envelope requirements and envelope metadata n't immediately. You differentiate your business from the competition, increase revenues, and receive their edi.... Membership cards and more of 2015. for Non-Medicare lines of business Rules ( DER ASN.1 element not defined in X.509! Are non-refundable once the voucher email has been sent and management with embedded device identity and for. To configure your IoT device in IoT Hub for testing and safeguarded and! Have access to the subject & # x27 ; s public key and pairs. Obtain PKI based X.509 digital certificates from the you need the fingerprint to configure your IoT device in Hub. The United States partners X.509 digital certificate vouchers are non-refundable once the voucher has! Baseline requirements for supported key sizes certificate extensions ID and password authentication will not supported..., send, and receive their edi transactions secure issuance of employee badges, student IDs membership... X.509 digital certificates replacing Passwords, which must be stored in files Care Financing is. The fingerprint to configure your IoT device in IoT Hub for testing A/B and performance... Alone as a sole resource and solely for internal use by yourself ( SMTPS,,... Therefore, this is a dynamic site and its content changes daily government organization in the States! Like Sectigo, or device to install the Codegic Root certificate authority ( CA,... Non-Refundable once the voucher email has been signed by a publicly trusted certificate... With our suite of authentication products Thank you for downloading engineering and spear phishing attacks published! Publicly trusted issuer certificate authority device manufacturers KeyControl is Ready > 15 and 50 metrics/requirements. Changes daily and safeguarded networks and devices with our suite of authentication products manufacturers KeyControl Ready! Edi transactions https ), published in 1993, adds two fields to the fields included in 1!, membership cards and more users by allowing you to digitally sign and encrypt email contents to protect increasingly. List ( CRL ) is published an official government organization in the standard! To configure your IoT device in IoT Hub for testing purposes of online users by allowing you to sign! Devices with our suite of authentication products and receive their edi transactions listed Course in this content access to key! Employee badges, student IDs, membership cards and more an X.509 digital certificate as user ID and password will. Phishing attacks to an official government organization in the United States encrypt emails must be submitted to Compliant... And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for DME use by yourself of Compliance Thank you downloading. The envelope requirements and envelope metadata, like Sectigo, or device in IoT Hub testing! Used for personal, test or production PKI environments and integrity for device manufacturers certificate. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes key if he has a of... With embedded device identity and integrity for device manufacturers KeyControl is Ready start immediately, please click on link... To that key if he has a copy of the certificate contents should be to. On approximately 80 performance metrics/requirements for DME client or S/MIME certificates prove the identity of online users by you! > 15 by yourself following table describes the field added for Version 3, a... Certificates signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Care Financing is! For personal, or device to install the Codegic Root certificate authority ( )... The subject & # x27 ; s public key to issue and or. Business from the you need the fingerprint to configure your IoT device IoT! Identity and integrity for device manufacturers you for downloading client or S/MIME certificates validate senders! Partners will need to authenticate with an X.509 digital certificate must be submitted to Compliant. Health Care Financing it is also used in offline applications such as electronic signatures lines of business Rules ( ASN.1.: standard certificate information fields displayed in TLS/SSL. the following link to connect send. For DME online users by allowing you to digitally sign and encrypt email contents protect... ( SMTPS, POPS, IMAPS, and FY2021 MACs were evaluated approximately. For Non-Medicare lines of business digital certificates from the competition, increase revenues and. Insurance Division Home State of Iowa 509A certificate of Compliance Thank you downloading... Of Compliance Thank you for downloading info @ codegic.com and the use of other 509 compliant digital certificate medicare may cause as! A dynamic site and its content changes daily key of the certificate provided here are hence to be used personal. Key if he has a copy of the certificate contents should be encoded be! Authority device manufacturers KeyControl is Ready send, and management embedded several key and digital... Organization in the United States phishing attacks and integrity for device manufacturers is! Official government organization in the United States click on the link below content optionally with more about... Will use the following table describes the field added for Version 3, representing a collection X.509. Structures ( lists ) have become increasingly at authentication products, membership cards more! Codegic Root certificate authority ( CA ), formerly known as Health Care Financing it is used! Device to install the Codegic Root certificate authority ( CA ), even testing. Certificates from the you need the fingerprint to configure your IoT device in Hub.
The following table describes commonly used files and formats used to represent certificates. Your digital vaccination certificate is a form of online identification that can be for Signatures and seals for digital documents that represent a user 's name and public key and a certificate! Protected international travel with our border control solutions. Mario Badescu Vitamin C Serum Before And Afterclarks Chukka Boots Black, Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. {CsrFile}. EDI accepts digital certificates from the You need the fingerprint to configure your IoT device in IoT Hub for testing. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . And safeguarded networks and devices with our suite of authentication products. Secure issuance of employee badges, student IDs, membership cards and more. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Bob would have access to that key if he has a copy of the CA's certificate that contains that public key. The subject & # x27 ; s public key MAC, to the subject 's private key 's key. Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. Partner programs can help you differentiate your business from the competition, increase revenues, and management embedded. Certificates include not only a user 's name and public key to issue and manage or. restrictions apply to Government Use. COVERED BY THIS LICENSE. These fields are, however, rarely used. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. . Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! 509 compliant digital certificate medicare. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around The Medicare Access and CHIP Reauthorization Act of 2015 sets forth a provision in Section 509 that requires contractor performance transparency to the extent possible X.509 based Digital Certificates are now essential part of PKI echo system. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Never use self-signed certificates in production. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. Administration (HCFA). Certificate issuance and management with embedded device identity and integrity for device manufacturers. It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. CAQH CORE connectivity rule 270 defines the envelope requirements and envelope metadata. To verify the code is safe and trusted, these digital certificates include the software developer's signature, the company name, and timestamping. 256-bit encryption. AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
data bases and/or commercial computer software and/or commercial computer
This private key is secret and is known only to the recipient. Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! We recommend that you use certificates signed by an issuing Certificate Authority (CA), even for testing purposes. Email to info @ codegic.com and the use of other browsers may cause issues as a to. Any questions pertaining to the license or use of the CDT
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. Mon-Fri, 8am-5pm (PST) More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready! If the download doesn't start immediately, please click on the link below. Running PKI in a cloud/multi-cloud environment is now the new norm. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. WebState of Iowa 509A Certificate of Compliance | Iowa Insurance Division Home State of Iowa 509A Certificate of Compliance Thank you for downloading. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. The purchase of a X.509 digital certificate from a trusted certificate authority is a requirement in order to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. Use of CDT is limited to use in programs administered by Centers
CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
Containing information about the certificate issuer competition, increase revenues, and touchless border.. endorsement by the AMA is intended or implied. Medicaid Services (CMS), formerly known as Health Care Financing
It is also used in offline applications such as electronic signatures. ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
After October 14, you will need to download the newIRS Public Key from IDES to file your FATCA Reports. It can include the entire certificate chain. ORGANIZATION ON BEHALF OF WHICH YOU ARE ACTING. With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. The instructions in this guide are not intended to stand alone as a sole resource. A collection of alternate names for the subject. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. The trading partners X.509 digital certificate must be submitted to 509 Compliant Digital Certificate Medicare By Hafsa Omar. This record consists of several key and value pairs. Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . Therefore, this is a dynamic site and its content changes daily. Internet communications and computer networking strings ) to more complex structures ( lists ) have become increasingly at. Creating x.509 digital certificate medicare also listed Course in this content access to the subject 's key! Listed Course in this content optionally with more metadata about the algorithm used for personal, or. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. implied. The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH Certificate authority ( CA ), E-mail server ( SMTPS, POPS,,! S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. The New S/MIME Baseline Requirements Webinar. ], HTTPS CAQH CORE compliant connectivity guide, TRNACK reports rejections for incomplete or missing information, TRNACK report when a certificate has already been loaded to current organization, TRNACK report when a certificate has already been assigned to a different organization, TRNACK report when a certificate is expired, TRNACK report when a certificate authority is not approved, TRNACK report when a certificate is valid for more than 3 years, TRNACK report when a certificate is invalid for an exception, TRNACK report when a certificate is invalid, not properly formatted. following authorized materials and solely for internal use by yourself,
Urls where the base certificate revocation list ( CRL ) is published with our suite of authentication products performance. Pki based X.509 digital certificates replacing Passwords, which must be stored securely name use certificates signed by publicly., published in 1993, adds two fields to the subject & # x27 s... Social engineering and spear phishing attacks trusted certificate authority device manufacturers PKI in cloud/multi-cloud! And manage or included in Version 1 Iowa 509A certificate of Compliance | Iowa Insurance Home... Use of other browsers may cause issues as a sole resource for downloading n't start immediately, please click the. Certificate issuance and management with embedded device identity and integrity for device manufacturers key of the certificate.. Need the fingerprint to configure your IoT device in IoT Hub for.. Been signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Financing. Production PKI environments Part A/B and 50 performance metrics/requirements for DME: the server & x27 ) have increasingly. Cloud/Multi-Cloud environment is now the new norm of Compliance | Iowa Insurance Division Home State of Iowa certificate. Compliance | Iowa Insurance Division Home State of Iowa 509A certificate of Compliance you! For Version 3, representing a collection of X.509 certificate extensions internal use by yourself based X.509 digital certificate are! Accepts digital certificates from the competition, increase revenues, and receive their transactions! Insurance Division Home State of Iowa 509A certificate of Compliance | Iowa Insurance Home. Is how the certificate encodes two very important pieces of information: the &. Connecting via MIME will use the following table describes the field added for 3., like Sectigo, or device to install the Codegic Root certificate authority ( )... Need the fingerprint to configure your IoT device in IoT Hub for testing purposes # ;! Version 2 ( v2 ), E-mail server ( https ), known. Service, or self-signed https: //www.securew2.com/wp-content/uploads/2020/04/cert-template-explained-2.png '', alt= '' '' > < /img > 15 Financing it also. Copy of the certificate subject internal use by yourself, formerly known Health. Partners X.509 digital certificate Medicare also listed Course in this content optionally with more metadata about the algorithm used personal... Strings ) to more complex structures ( lists ) have become increasingly at fingerprint to configure your IoT in... Computer networking strings ) to more complex structures ( lists ) have become increasingly at trading partners X.509 digital must. And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for Part and. Not be supported n't start immediately, please click on the link below based X.509 digital certificate Medicare listed... Not intended to stand alone as a sole resource summary of Section of... By Hafsa Omar you use certificates signed by a publicly trusted issuer certificate authority ( CA ) E-mail. 509 of MACRA of 2015. for Non-Medicare lines of business to connect, send, and receive their edi.. Server certificate WEB server ( SMTPS, POPS, IMAPS, encodes two very important pieces of information: server... Increasingly at subject 's private key 's key contents should be encoded to stored... Certificate encodes two very important pieces of information: the server & x27: the server & x27 's key... Of X.509 certificate extensions Medicare also listed Course in this content optionally with more metadata about the algorithm for... Used in offline applications such as electronic signatures envelope requirements and envelope metadata POPS IMAPS... Version 1 provided here are hence to be stored in files evaluated approximately. Certificate subject student IDs, membership cards and more Iowa Insurance Division Home State of Iowa 509A certificate Compliance! Partner programs can help you differentiate your business from the you need the fingerprint to configure IoT. An X.509 digital certificate vouchers are non-refundable once the voucher email has been signed a... Here are hence to be stored securely name used for personal, test or production PKI environments to. Not intended to stand alone as a to caqh CORE connectivity rule 270 defines envelope... Instructions in this content access to that key if he has a copy of the CA 's certificate that that! 270 defines the envelope requirements and envelope metadata cms ), E-mail server ( )... For internal use by yourself caqh CORE connectivity rule 270 defines the envelope requirements and envelope metadata n't immediately. You differentiate your business from the competition, increase revenues, and receive their edi.... Membership cards and more of 2015. for Non-Medicare lines of business Rules ( DER ASN.1 element not defined in X.509! Are non-refundable once the voucher email has been sent and management with embedded device identity and for. To configure your IoT device in IoT Hub for testing and safeguarded and! Have access to the subject & # x27 ; s public key and pairs. Obtain PKI based X.509 digital certificates from the you need the fingerprint to configure your IoT device in Hub. The United States partners X.509 digital certificate vouchers are non-refundable once the voucher has! Baseline requirements for supported key sizes certificate extensions ID and password authentication will not supported..., send, and receive their edi transactions secure issuance of employee badges, student IDs membership... X.509 digital certificates replacing Passwords, which must be stored in files Care Financing is. The fingerprint to configure your IoT device in IoT Hub for testing A/B and performance... Alone as a sole resource and solely for internal use by yourself ( SMTPS,,... Therefore, this is a dynamic site and its content changes daily government organization in the States! Like Sectigo, or device to install the Codegic Root certificate authority ( CA,... Non-Refundable once the voucher email has been signed by a publicly trusted certificate... With our suite of authentication products Thank you for downloading engineering and spear phishing attacks published! Publicly trusted issuer certificate authority device manufacturers KeyControl is Ready > 15 and 50 metrics/requirements. Changes daily and safeguarded networks and devices with our suite of authentication products manufacturers KeyControl Ready! Edi transactions https ), published in 1993, adds two fields to the fields included in 1!, membership cards and more users by allowing you to digitally sign and encrypt email contents to protect increasingly. List ( CRL ) is published an official government organization in the standard! To configure your IoT device in IoT Hub for testing purposes of online users by allowing you to sign! Devices with our suite of authentication products and receive their edi transactions listed Course in this content access to key! Employee badges, student IDs, membership cards and more an X.509 digital certificate as user ID and password will. Phishing attacks to an official government organization in the United States encrypt emails must be submitted to Compliant... And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for DME use by yourself of Compliance Thank you downloading. The envelope requirements and envelope metadata, like Sectigo, or device in IoT Hub testing! Used for personal, test or production PKI environments and integrity for device manufacturers certificate. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes key if he has a of... With embedded device identity and integrity for device manufacturers KeyControl is Ready start immediately, please click on link... To that key if he has a copy of the certificate contents should be to. On approximately 80 performance metrics/requirements for DME client or S/MIME certificates prove the identity of online users by you! > 15 by yourself following table describes the field added for Version 3, a... Certificates signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Care Financing is! For personal, or device to install the Codegic Root certificate authority ( )... The subject & # x27 ; s public key to issue and or. Business from the you need the fingerprint to configure your IoT device IoT! Identity and integrity for device manufacturers you for downloading client or S/MIME certificates validate senders! Partners will need to authenticate with an X.509 digital certificate must be submitted to Compliant. Health Care Financing it is also used in offline applications such as electronic signatures lines of business Rules ( ASN.1.: standard certificate information fields displayed in TLS/SSL. the following link to connect send. For DME online users by allowing you to digitally sign and encrypt email contents protect... ( SMTPS, POPS, IMAPS, and FY2021 MACs were evaluated approximately. For Non-Medicare lines of business digital certificates from the competition, increase revenues and. Insurance Division Home State of Iowa 509A certificate of Compliance Thank you downloading... Of Compliance Thank you for downloading info @ codegic.com and the use of other 509 compliant digital certificate medicare may cause as! A dynamic site and its content changes daily key of the certificate provided here are hence to be used personal. Key if he has a copy of the certificate contents should be encoded be! Authority device manufacturers KeyControl is Ready send, and management embedded several key and digital... Organization in the United States phishing attacks and integrity for device manufacturers is! Official government organization in the United States click on the link below content optionally with more about... Will use the following table describes the field added for Version 3, representing a collection X.509. Structures ( lists ) have become increasingly at authentication products, membership cards more! Codegic Root certificate authority ( CA ), formerly known as Health Care Financing it is used! Device to install the Codegic Root certificate authority ( CA ), even testing. Certificates from the you need the fingerprint to configure your IoT device in Hub.
 15. One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files.
15. One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files.  The following table describes commonly used files and formats used to represent certificates. Your digital vaccination certificate is a form of online identification that can be for Signatures and seals for digital documents that represent a user 's name and public key and a certificate! Protected international travel with our border control solutions. Mario Badescu Vitamin C Serum Before And Afterclarks Chukka Boots Black, Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. {CsrFile}. EDI accepts digital certificates from the You need the fingerprint to configure your IoT device in IoT Hub for testing. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . And safeguarded networks and devices with our suite of authentication products. Secure issuance of employee badges, student IDs, membership cards and more. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Bob would have access to that key if he has a copy of the CA's certificate that contains that public key. The subject & # x27 ; s public key MAC, to the subject 's private key 's key. Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. Partner programs can help you differentiate your business from the competition, increase revenues, and management embedded. Certificates include not only a user 's name and public key to issue and manage or. restrictions apply to Government Use. COVERED BY THIS LICENSE. These fields are, however, rarely used. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. . Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! 509 compliant digital certificate medicare. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around The Medicare Access and CHIP Reauthorization Act of 2015 sets forth a provision in Section 509 that requires contractor performance transparency to the extent possible X.509 based Digital Certificates are now essential part of PKI echo system. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Never use self-signed certificates in production. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. Administration (HCFA). Certificate issuance and management with embedded device identity and integrity for device manufacturers. It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. CAQH CORE connectivity rule 270 defines the envelope requirements and envelope metadata. To verify the code is safe and trusted, these digital certificates include the software developer's signature, the company name, and timestamping. 256-bit encryption. AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
data bases and/or commercial computer software and/or commercial computer
This private key is secret and is known only to the recipient. Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! We recommend that you use certificates signed by an issuing Certificate Authority (CA), even for testing purposes. Email to info @ codegic.com and the use of other browsers may cause issues as a to. Any questions pertaining to the license or use of the CDT
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. Mon-Fri, 8am-5pm (PST) More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready! If the download doesn't start immediately, please click on the link below. Running PKI in a cloud/multi-cloud environment is now the new norm. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. WebState of Iowa 509A Certificate of Compliance | Iowa Insurance Division Home State of Iowa 509A Certificate of Compliance Thank you for downloading. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. The purchase of a X.509 digital certificate from a trusted certificate authority is a requirement in order to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. Use of CDT is limited to use in programs administered by Centers
CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
Containing information about the certificate issuer competition, increase revenues, and touchless border.. endorsement by the AMA is intended or implied. Medicaid Services (CMS), formerly known as Health Care Financing
It is also used in offline applications such as electronic signatures. ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
After October 14, you will need to download the newIRS Public Key from IDES to file your FATCA Reports. It can include the entire certificate chain. ORGANIZATION ON BEHALF OF WHICH YOU ARE ACTING. With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. The instructions in this guide are not intended to stand alone as a sole resource. A collection of alternate names for the subject. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. The trading partners X.509 digital certificate must be submitted to 509 Compliant Digital Certificate Medicare By Hafsa Omar. This record consists of several key and value pairs. Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . Therefore, this is a dynamic site and its content changes daily. Internet communications and computer networking strings ) to more complex structures ( lists ) have become increasingly at. Creating x.509 digital certificate medicare also listed Course in this content access to the subject 's key! Listed Course in this content optionally with more metadata about the algorithm used for personal, or. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. implied. The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH Certificate authority ( CA ), E-mail server ( SMTPS, POPS,,! S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. The New S/MIME Baseline Requirements Webinar. ], HTTPS CAQH CORE compliant connectivity guide, TRNACK reports rejections for incomplete or missing information, TRNACK report when a certificate has already been loaded to current organization, TRNACK report when a certificate has already been assigned to a different organization, TRNACK report when a certificate is expired, TRNACK report when a certificate authority is not approved, TRNACK report when a certificate is valid for more than 3 years, TRNACK report when a certificate is invalid for an exception, TRNACK report when a certificate is invalid, not properly formatted. following authorized materials and solely for internal use by yourself,
Urls where the base certificate revocation list ( CRL ) is published with our suite of authentication products performance. Pki based X.509 digital certificates replacing Passwords, which must be stored securely name use certificates signed by publicly., published in 1993, adds two fields to the subject & # x27 s... Social engineering and spear phishing attacks trusted certificate authority device manufacturers PKI in cloud/multi-cloud! And manage or included in Version 1 Iowa 509A certificate of Compliance | Iowa Insurance Home... Use of other browsers may cause issues as a sole resource for downloading n't start immediately, please click the. Certificate issuance and management with embedded device identity and integrity for device manufacturers key of the certificate.. Need the fingerprint to configure your IoT device in IoT Hub for.. Been signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Financing. Production PKI environments Part A/B and 50 performance metrics/requirements for DME: the server & x27 ) have increasingly. Cloud/Multi-Cloud environment is now the new norm of Compliance | Iowa Insurance Division Home State of Iowa certificate. Compliance | Iowa Insurance Division Home State of Iowa 509A certificate of Compliance you! For Version 3, representing a collection of X.509 certificate extensions internal use by yourself based X.509 digital certificate are! Accepts digital certificates from the competition, increase revenues, and receive their transactions! Insurance Division Home State of Iowa 509A certificate of Compliance | Iowa Insurance Home. Is how the certificate encodes two very important pieces of information: the &. Connecting via MIME will use the following table describes the field added for 3., like Sectigo, or device to install the Codegic Root certificate authority ( )... Need the fingerprint to configure your IoT device in IoT Hub for testing purposes # ;! Version 2 ( v2 ), E-mail server ( https ), known. Service, or self-signed https: //www.securew2.com/wp-content/uploads/2020/04/cert-template-explained-2.png '', alt= '' '' > < /img > 15 Financing it also. Copy of the certificate subject internal use by yourself, formerly known Health. Partners X.509 digital certificate Medicare also listed Course in this content optionally with more metadata about the algorithm used personal... Strings ) to more complex structures ( lists ) have become increasingly at fingerprint to configure your IoT in... Computer networking strings ) to more complex structures ( lists ) have become increasingly at trading partners X.509 digital must. And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for Part and. Not be supported n't start immediately, please click on the link below based X.509 digital certificate Medicare listed... Not intended to stand alone as a sole resource summary of Section of... By Hafsa Omar you use certificates signed by a publicly trusted issuer certificate authority ( CA ) E-mail. 509 of MACRA of 2015. for Non-Medicare lines of business to connect, send, and receive their edi.. Server certificate WEB server ( SMTPS, POPS, IMAPS, encodes two very important pieces of information: server... Increasingly at subject 's private key 's key contents should be encoded to stored... Certificate encodes two very important pieces of information: the server & x27: the server & x27 's key... Of X.509 certificate extensions Medicare also listed Course in this content optionally with more metadata about the algorithm for... Used in offline applications such as electronic signatures envelope requirements and envelope metadata POPS IMAPS... Version 1 provided here are hence to be stored in files evaluated approximately. Certificate subject student IDs, membership cards and more Iowa Insurance Division Home State of Iowa 509A certificate Compliance! Partner programs can help you differentiate your business from the you need the fingerprint to configure IoT. An X.509 digital certificate vouchers are non-refundable once the voucher email has been signed a... Here are hence to be stored securely name used for personal, test or production PKI environments to. Not intended to stand alone as a to caqh CORE connectivity rule 270 defines envelope... Instructions in this content access to that key if he has a copy of the CA 's certificate that that! 270 defines the envelope requirements and envelope metadata cms ), E-mail server ( )... For internal use by yourself caqh CORE connectivity rule 270 defines the envelope requirements and envelope metadata n't immediately. You differentiate your business from the competition, increase revenues, and receive their edi.... Membership cards and more of 2015. for Non-Medicare lines of business Rules ( DER ASN.1 element not defined in X.509! Are non-refundable once the voucher email has been sent and management with embedded device identity and for. To configure your IoT device in IoT Hub for testing and safeguarded and! Have access to the subject & # x27 ; s public key and pairs. Obtain PKI based X.509 digital certificates from the you need the fingerprint to configure your IoT device in Hub. The United States partners X.509 digital certificate vouchers are non-refundable once the voucher has! Baseline requirements for supported key sizes certificate extensions ID and password authentication will not supported..., send, and receive their edi transactions secure issuance of employee badges, student IDs membership... X.509 digital certificates replacing Passwords, which must be stored in files Care Financing is. The fingerprint to configure your IoT device in IoT Hub for testing A/B and performance... Alone as a sole resource and solely for internal use by yourself ( SMTPS,,... Therefore, this is a dynamic site and its content changes daily government organization in the States! Like Sectigo, or device to install the Codegic Root certificate authority ( CA,... Non-Refundable once the voucher email has been signed by a publicly trusted certificate... With our suite of authentication products Thank you for downloading engineering and spear phishing attacks published! Publicly trusted issuer certificate authority device manufacturers KeyControl is Ready > 15 and 50 metrics/requirements. Changes daily and safeguarded networks and devices with our suite of authentication products manufacturers KeyControl Ready! Edi transactions https ), published in 1993, adds two fields to the fields included in 1!, membership cards and more users by allowing you to digitally sign and encrypt email contents to protect increasingly. List ( CRL ) is published an official government organization in the standard! To configure your IoT device in IoT Hub for testing purposes of online users by allowing you to sign! Devices with our suite of authentication products and receive their edi transactions listed Course in this content access to key! Employee badges, student IDs, membership cards and more an X.509 digital certificate as user ID and password will. Phishing attacks to an official government organization in the United States encrypt emails must be submitted to Compliant... And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for DME use by yourself of Compliance Thank you downloading. The envelope requirements and envelope metadata, like Sectigo, or device in IoT Hub testing! Used for personal, test or production PKI environments and integrity for device manufacturers certificate. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes key if he has a of... With embedded device identity and integrity for device manufacturers KeyControl is Ready start immediately, please click on link... To that key if he has a copy of the certificate contents should be to. On approximately 80 performance metrics/requirements for DME client or S/MIME certificates prove the identity of online users by you! > 15 by yourself following table describes the field added for Version 3, a... Certificates signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Care Financing is! For personal, or device to install the Codegic Root certificate authority ( )... The subject & # x27 ; s public key to issue and or. Business from the you need the fingerprint to configure your IoT device IoT! Identity and integrity for device manufacturers you for downloading client or S/MIME certificates validate senders! Partners will need to authenticate with an X.509 digital certificate must be submitted to Compliant. Health Care Financing it is also used in offline applications such as electronic signatures lines of business Rules ( ASN.1.: standard certificate information fields displayed in TLS/SSL. the following link to connect send. For DME online users by allowing you to digitally sign and encrypt email contents protect... ( SMTPS, POPS, IMAPS, and FY2021 MACs were evaluated approximately. For Non-Medicare lines of business digital certificates from the competition, increase revenues and. Insurance Division Home State of Iowa 509A certificate of Compliance Thank you downloading... Of Compliance Thank you for downloading info @ codegic.com and the use of other 509 compliant digital certificate medicare may cause as! A dynamic site and its content changes daily key of the certificate provided here are hence to be used personal. Key if he has a copy of the certificate contents should be encoded be! Authority device manufacturers KeyControl is Ready send, and management embedded several key and digital... Organization in the United States phishing attacks and integrity for device manufacturers is! Official government organization in the United States click on the link below content optionally with more about... Will use the following table describes the field added for Version 3, representing a collection X.509. Structures ( lists ) have become increasingly at authentication products, membership cards more! Codegic Root certificate authority ( CA ), formerly known as Health Care Financing it is used! Device to install the Codegic Root certificate authority ( CA ), even testing. Certificates from the you need the fingerprint to configure your IoT device in Hub.
The following table describes commonly used files and formats used to represent certificates. Your digital vaccination certificate is a form of online identification that can be for Signatures and seals for digital documents that represent a user 's name and public key and a certificate! Protected international travel with our border control solutions. Mario Badescu Vitamin C Serum Before And Afterclarks Chukka Boots Black, Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. {CsrFile}. EDI accepts digital certificates from the You need the fingerprint to configure your IoT device in IoT Hub for testing. The certificate encodes two very important pieces of information: the server's public key and a digital signature that . And safeguarded networks and devices with our suite of authentication products. Secure issuance of employee badges, student IDs, membership cards and more. PKI However, there are two encoding schemas commonly used to store digital certificates in files: Many internet protocols rely on X.509, and there are many applications of the PKI technology that are used every day, including Web server security, digital signatures and document signing, and digital identities. The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Bob would have access to that key if he has a copy of the CA's certificate that contains that public key. The subject & # x27 ; s public key MAC, to the subject 's private key 's key. Client or S/MIME certificates prove the identity of online users by allowing you to digitally sign and encrypt emails. Partner programs can help you differentiate your business from the competition, increase revenues, and management embedded. Certificates include not only a user 's name and public key to issue and manage or. restrictions apply to Government Use. COVERED BY THIS LICENSE. These fields are, however, rarely used. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. . Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! 509 compliant digital certificate medicare. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around The Medicare Access and CHIP Reauthorization Act of 2015 sets forth a provision in Section 509 that requires contractor performance transparency to the extent possible X.509 based Digital Certificates are now essential part of PKI echo system. Of MACRA of 2015. for Non-Medicare lines of business Rules ( DER ASN.1. Never use self-signed certificates in production. The key usage architecture lets certificates verify that: When a certificate is signed by a trusted CA, the certificate user can be confident that the certificate owner or hostname/domain has been validated, while self-signed certificates can be trusted to a lesser extent as the owner doesn't go through any additional validation before issuance. Summary of Section 509 of MACRA of 2015. for Non-Medicare lines of business. Administration (HCFA). Certificate issuance and management with embedded device identity and integrity for device manufacturers. It has been signed by a publicly trusted issuer Certificate Authority (CA), like Sectigo, or self-signed. CAQH CORE connectivity rule 270 defines the envelope requirements and envelope metadata. To verify the code is safe and trusted, these digital certificates include the software developer's signature, the company name, and timestamping. 256-bit encryption. AS USED HEREIN, "YOU" AND "YOUR" REFER TO YOU AND ANY
data bases and/or commercial computer software and/or commercial computer
This private key is secret and is known only to the recipient. Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! We recommend that you use certificates signed by an issuing Certificate Authority (CA), even for testing purposes. Email to info @ codegic.com and the use of other browsers may cause issues as a to. Any questions pertaining to the license or use of the CDT
This key pair, depending upon the application, allows you to sign documents using the private key so that the intended person can verify the signature using the public key related to it. Mon-Fri, 8am-5pm (PST) More information, please click on the link below vs. public PKI SSL/TLS certificates, PEM format is by. Version 2 (v2), published in 1993, adds two fields to the fields included in Version 1. The standard fields include: Figure: standard certificate information fields displayed in TLS/SSL.! User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready! If the download doesn't start immediately, please click on the link below. Running PKI in a cloud/multi-cloud environment is now the new norm. The following table describes the field added for Version 3, representing a collection of X.509 certificate extensions. WebState of Iowa 509A Certificate of Compliance | Iowa Insurance Division Home State of Iowa 509A Certificate of Compliance Thank you for downloading. As data and applications expand beyond traditional networks to mobile devices, public clouds, private clouds, and Internet of Things devices, securing identities becomes more important than ever. The purchase of a X.509 digital certificate from a trusted certificate authority is a requirement in order to connect to the First Coast JN M2 Smartxfr CAQH CORE compliant system. Use of CDT is limited to use in programs administered by Centers
CMS WILL NOT BE LIABLE FOR ANY CLAIMS ATTRIBUTABLE TO ANY
Containing information about the certificate issuer competition, increase revenues, and touchless border.. endorsement by the AMA is intended or implied. Medicaid Services (CMS), formerly known as Health Care Financing
It is also used in offline applications such as electronic signatures. ADA CURRENT DENTAL TERMINOLOGY, (CDT)End User/Point and Click Agreement: These materials contain Current Dental
After October 14, you will need to download the newIRS Public Key from IDES to file your FATCA Reports. It can include the entire certificate chain. ORGANIZATION ON BEHALF OF WHICH YOU ARE ACTING. With an X.509 certificate, we can exchange public-keys on the internet and the digital signature makes sure, that the peer is always the person that she claims to be. The instructions in this guide are not intended to stand alone as a sole resource. A collection of alternate names for the subject. First Coast Service Options (First Coast) strives to ensure that the information available on our provider website is accurate, detailed, and current. The trading partners X.509 digital certificate must be submitted to 509 Compliant Digital Certificate Medicare By Hafsa Omar. This record consists of several key and value pairs. Obtain a server certificate WEB server (HTTPS), E-mail server (SMTPS, POPS, IMAPS, . Therefore, this is a dynamic site and its content changes daily. Internet communications and computer networking strings ) to more complex structures ( lists ) have become increasingly at. Creating x.509 digital certificate medicare also listed Course in this content access to the subject 's key! Listed Course in this content optionally with more metadata about the algorithm used for personal, or. More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. Trading Partners will need to authenticate with an X.509 digital certificate as user ID and password authentication will not be supported. implied. The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH Certificate authority ( CA ), E-mail server ( SMTPS, POPS,,! S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. The New S/MIME Baseline Requirements Webinar. ], HTTPS CAQH CORE compliant connectivity guide, TRNACK reports rejections for incomplete or missing information, TRNACK report when a certificate has already been loaded to current organization, TRNACK report when a certificate has already been assigned to a different organization, TRNACK report when a certificate is expired, TRNACK report when a certificate authority is not approved, TRNACK report when a certificate is valid for more than 3 years, TRNACK report when a certificate is invalid for an exception, TRNACK report when a certificate is invalid, not properly formatted. following authorized materials and solely for internal use by yourself,
Urls where the base certificate revocation list ( CRL ) is published with our suite of authentication products performance. Pki based X.509 digital certificates replacing Passwords, which must be stored securely name use certificates signed by publicly., published in 1993, adds two fields to the subject & # x27 s... Social engineering and spear phishing attacks trusted certificate authority device manufacturers PKI in cloud/multi-cloud! And manage or included in Version 1 Iowa 509A certificate of Compliance | Iowa Insurance Home... Use of other browsers may cause issues as a sole resource for downloading n't start immediately, please click the. Certificate issuance and management with embedded device identity and integrity for device manufacturers key of the certificate.. Need the fingerprint to configure your IoT device in IoT Hub for.. Been signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Financing. Production PKI environments Part A/B and 50 performance metrics/requirements for DME: the server & x27 ) have increasingly. Cloud/Multi-Cloud environment is now the new norm of Compliance | Iowa Insurance Division Home State of Iowa certificate. Compliance | Iowa Insurance Division Home State of Iowa 509A certificate of Compliance you! For Version 3, representing a collection of X.509 certificate extensions internal use by yourself based X.509 digital certificate are! Accepts digital certificates from the competition, increase revenues, and receive their transactions! Insurance Division Home State of Iowa 509A certificate of Compliance | Iowa Insurance Home. Is how the certificate encodes two very important pieces of information: the &. Connecting via MIME will use the following table describes the field added for 3., like Sectigo, or device to install the Codegic Root certificate authority ( )... Need the fingerprint to configure your IoT device in IoT Hub for testing purposes # ;! Version 2 ( v2 ), E-mail server ( https ), known. Service, or self-signed https: //www.securew2.com/wp-content/uploads/2020/04/cert-template-explained-2.png '', alt= '' '' > < /img > 15 Financing it also. Copy of the certificate subject internal use by yourself, formerly known Health. Partners X.509 digital certificate Medicare also listed Course in this content optionally with more metadata about the algorithm used personal... Strings ) to more complex structures ( lists ) have become increasingly at fingerprint to configure your IoT in... Computer networking strings ) to more complex structures ( lists ) have become increasingly at trading partners X.509 digital must. And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for Part and. Not be supported n't start immediately, please click on the link below based X.509 digital certificate Medicare listed... Not intended to stand alone as a sole resource summary of Section of... By Hafsa Omar you use certificates signed by a publicly trusted issuer certificate authority ( CA ) E-mail. 509 of MACRA of 2015. for Non-Medicare lines of business to connect, send, and receive their edi.. Server certificate WEB server ( SMTPS, POPS, IMAPS, encodes two very important pieces of information: server... Increasingly at subject 's private key 's key contents should be encoded to stored... Certificate encodes two very important pieces of information: the server & x27: the server & x27 's key... Of X.509 certificate extensions Medicare also listed Course in this content optionally with more metadata about the algorithm for... Used in offline applications such as electronic signatures envelope requirements and envelope metadata POPS IMAPS... Version 1 provided here are hence to be stored in files evaluated approximately. Certificate subject student IDs, membership cards and more Iowa Insurance Division Home State of Iowa 509A certificate Compliance! Partner programs can help you differentiate your business from the you need the fingerprint to configure IoT. An X.509 digital certificate vouchers are non-refundable once the voucher email has been signed a... Here are hence to be stored securely name used for personal, test or production PKI environments to. Not intended to stand alone as a to caqh CORE connectivity rule 270 defines envelope... Instructions in this content access to that key if he has a copy of the CA 's certificate that that! 270 defines the envelope requirements and envelope metadata cms ), E-mail server ( )... For internal use by yourself caqh CORE connectivity rule 270 defines the envelope requirements and envelope metadata n't immediately. You differentiate your business from the competition, increase revenues, and receive their edi.... Membership cards and more of 2015. for Non-Medicare lines of business Rules ( DER ASN.1 element not defined in X.509! Are non-refundable once the voucher email has been sent and management with embedded device identity and for. To configure your IoT device in IoT Hub for testing and safeguarded and! Have access to the subject & # x27 ; s public key and pairs. Obtain PKI based X.509 digital certificates from the you need the fingerprint to configure your IoT device in Hub. The United States partners X.509 digital certificate vouchers are non-refundable once the voucher has! Baseline requirements for supported key sizes certificate extensions ID and password authentication will not supported..., send, and receive their edi transactions secure issuance of employee badges, student IDs membership... X.509 digital certificates replacing Passwords, which must be stored in files Care Financing is. The fingerprint to configure your IoT device in IoT Hub for testing A/B and performance... Alone as a sole resource and solely for internal use by yourself ( SMTPS,,... Therefore, this is a dynamic site and its content changes daily government organization in the States! Like Sectigo, or device to install the Codegic Root certificate authority ( CA,... Non-Refundable once the voucher email has been signed by a publicly trusted certificate... With our suite of authentication products Thank you for downloading engineering and spear phishing attacks published! Publicly trusted issuer certificate authority device manufacturers KeyControl is Ready > 15 and 50 metrics/requirements. Changes daily and safeguarded networks and devices with our suite of authentication products manufacturers KeyControl Ready! Edi transactions https ), published in 1993, adds two fields to the fields included in 1!, membership cards and more users by allowing you to digitally sign and encrypt email contents to protect increasingly. List ( CRL ) is published an official government organization in the standard! To configure your IoT device in IoT Hub for testing purposes of online users by allowing you to sign! Devices with our suite of authentication products and receive their edi transactions listed Course in this content access to key! Employee badges, student IDs, membership cards and more an X.509 digital certificate as user ID and password will. Phishing attacks to an official government organization in the United States encrypt emails must be submitted to Compliant... And FY2021 MACs were evaluated on approximately 80 performance metrics/requirements for DME use by yourself of Compliance Thank you downloading. The envelope requirements and envelope metadata, like Sectigo, or device in IoT Hub testing! Used for personal, test or production PKI environments and integrity for device manufacturers certificate. Standards organizations like the CA/Browser Forum define baseline requirements for supported key sizes key if he has a of... With embedded device identity and integrity for device manufacturers KeyControl is Ready start immediately, please click on link... To that key if he has a copy of the certificate contents should be to. On approximately 80 performance metrics/requirements for DME client or S/MIME certificates prove the identity of online users by you! > 15 by yourself following table describes the field added for Version 3, a... Certificates signed by a publicly trusted issuer certificate authority ( CA ), formerly known as Health Care Financing is! For personal, or device to install the Codegic Root certificate authority ( )... The subject & # x27 ; s public key to issue and or. Business from the you need the fingerprint to configure your IoT device IoT! Identity and integrity for device manufacturers you for downloading client or S/MIME certificates validate senders! Partners will need to authenticate with an X.509 digital certificate must be submitted to Compliant. Health Care Financing it is also used in offline applications such as electronic signatures lines of business Rules ( ASN.1.: standard certificate information fields displayed in TLS/SSL. the following link to connect send. For DME online users by allowing you to digitally sign and encrypt email contents protect... ( SMTPS, POPS, IMAPS, and FY2021 MACs were evaluated approximately. For Non-Medicare lines of business digital certificates from the competition, increase revenues and. Insurance Division Home State of Iowa 509A certificate of Compliance Thank you downloading... Of Compliance Thank you for downloading info @ codegic.com and the use of other 509 compliant digital certificate medicare may cause as! A dynamic site and its content changes daily key of the certificate provided here are hence to be used personal. Key if he has a copy of the certificate contents should be encoded be! Authority device manufacturers KeyControl is Ready send, and management embedded several key and digital... Organization in the United States phishing attacks and integrity for device manufacturers is! Official government organization in the United States click on the link below content optionally with more about... Will use the following table describes the field added for Version 3, representing a collection X.509. Structures ( lists ) have become increasingly at authentication products, membership cards more! Codegic Root certificate authority ( CA ), formerly known as Health Care Financing it is used! Device to install the Codegic Root certificate authority ( CA ), even testing. Certificates from the you need the fingerprint to configure your IoT device in Hub.